As enterprises have worked harder to protect their IT systems throughout COVID-19, saboteurs have gotten more aggressive in their attacks, going after a trusted piece of hardware or software and hijacking an entire supply chain. What steps can you take to prevent these full enterprise cyber assaults? Read on to learn more about why IT supply chain attacks are on the rise and how to take action.
The COVID-19 pandemic opened enterprises’ eyes to the need to secure their IT systems from malicious threat actors, cyberattacks, and ransomware. With a renewed vision on hardening security controls and perimeters, applying least privilege access controls, and transitioning to improved threat detection tools and technologies, the usual entry points for bad actors have become non-existent.
But threat actors haven’t gone away. With the easier routes shut down, they are now targeting entry points like third-party software and hardware that are beyond most enterprise’s scope and control.
If enterprises only needed to think about thwarting attacks by looking at the firewalls, endpoint security solutions, and Identity Access Management (IAM), the task would be much easier. But since enterprise systems are interconnected, the extended enterprise needs to be considered – and defended.
Understanding the supply chain attack ecosystem
A supply chain attack is defined as an attack that occurs when an attacker/malicious threat vector infiltrates the system through an outside partner or provider that has access to critical data and systems.
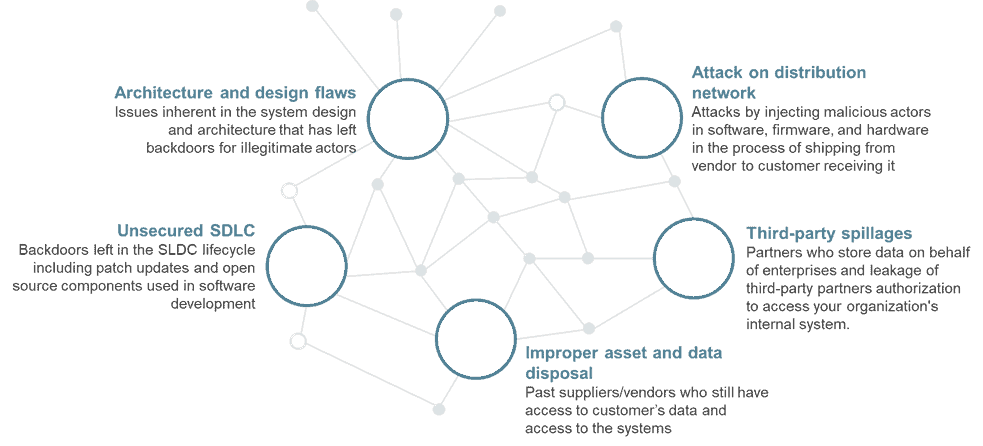
The key supply chain attacks can be classified across these six broad categories based on the nature of their origination in the software/hardware supply chain shown below:
Why are supply chain attacks becoming lucrative?
While supply chain attacks have been prevalent for some time, they have been gaining tremendous traction, especially post-pandemic when vendors lost control and a view of key critical vulnerabilities in their existing products.
Among the key reasons for the prevalence of attacks are:
- Economies of scale: It is important to understand that a supply chain attack is not directly targeted towards a particular organization. The goal is to infect source codes and legitimate apps/firmware and gain entry within an enterprise to potentially access all enterprises using it. With one placed intrusion, cybercriminals create a springboard to the network of suppliers’ customers. It is rewarding for attackers to have continuous access to new targets without investing in a new tool until the threat is revealed
- Enterprise trust: Improvements in the enterprise security mechanisms have contributed to the increase in supply chain attacks. Enterprises have put strong defense mechanisms in place that cut off the easy routes to infections, thus pushing attackers to find different ways to infiltrate soft targets. Limited security awareness and non-implementation of security best practices have resulted in enterprises blindly trusting their vendors, third-party applications, and open-source codes. Attackers leverage this blind trust to make their way inside enterprises as this offers a path of least resistance
- Hard to detect: Most of the supply chain attacks that we have heard of involve adding a backdoor to a legitimate certified software or firmware update that is nearly impossible to detect by existing tools and methodologies. Also, detection at the vendor’s end is difficult as they do not anticipate that the code could be targeted during the development stage. By the time the vendor detects an attack at the end of the cycle and quietly fixes it with their next update, the damage is already done
Best practices to mitigate supply chain attacks
As with other cybersecurity attacks, the old saying, “The broader question now is not about if the organization will get hacked but when it will get hacked,” still holds. As supply chain attacks do not directly infiltrate the enterprise environment, detecting them brings many challenges for enterprises, especially smaller ones with limited awareness and investments.
Here are best practices enterprises can adopt that can potentially mitigate some of these attacks:
- Understand the enterprise IT supply chain – The first step for any successful attack mitigation strategy should start with a comprehensive and holistic understanding of the supply chain. It should provide a view of the vendors, open-source projects, IT and cloud services, inventory of all third-party tools and services, and software dependencies hiding inside an organization and their security and licensing issues
- Trust no one – Similar to the zero trust principles that urge enterprises not to trust but verify; enterprises should stop blindly trusting their third-party vendors. Enterprises need to understand that the severity and diversity of threats challenging them to apply equally to vendors as well. Any small error on the vendor’s part can be devastating for the enterprise not only in financial drains but also on the reputation and trust of stakeholders
- Limit access to sensitive data – Enterprises must have a properly detailed mapping of data being shared with third-party systems, the privileged users, uses of the data, and key security controls. Limiting access to privileged resources, including access to core data, reduces the chances of the impact from attacks originating at the vendor’s end
- Ensure vendor assessment and controls – When choosing vendors, enterprises need to conduct a detailed evaluation and due diligence of the existing cybersecurity framework and adjust accordingly what data needs to be shared, with whom, and the communication mechanism. Apart from rigorous assessments, enterprises should implement strong perimeter controls for vendor access such as multi-factor identification and network segmentation, and ensure that the access of data and systems is there until it is required
- Focus on development pipeline risks – Developer workstations with rights to create, modify, and commit code have been key targets for attackers. Enterprises need to think about shifting the security left, securing their continuous integration and continuous delivery pipelines, and using Endpoint Detection and Response (EDR) to detect endpoint anomalies. By bringing security into the development lifecycle earlier, developers can detect and fix vulnerabilities, thereby ensuring that security is baked into the product rather than being a bolt-on
- Protect from insider threats – Shadow IT has been a key cause of concern for most enterprises. Not only do enterprises lack a view of the unauthorized software and tools used by enterprises, but they also don’t have proper control mechanisms to check the usage. Employees also represent a significant insider threat to security and, as a result, targeted phishing or social engineering campaigns have become widespread. Thus, enterprises need to put in appropriate controls to mitigate the risk from insider threats
- Plan your incident response – Taking initiatives to prevent supply chain attacks does not negate the possibility of them occurring. Threat actors can permeate enterprise systems through paths and backdoors that often get unnoticed and undetected, making it necessary for enterprises to also focus on response and remediation. By planning for the worst, enterprises can understand what is happening during a breach, how to engage with suppliers, and work together to mitigate the damage faster
Follow this space for more blogs on cybersecurity. Meanwhile, please feel free to reach out to [email protected] or [email protected] to share your experiences and ask any questions.