Blog
Palo Alto Networks’ Acquisition of CyberArk Signals a New Era for Identity and Access Management and Cybersecurity Titans

In what is being called one of the boldest deals in cybersecurity for years, Palo Alto Networks (PANW) announced its acquisition of CyberArk for an eye-watering $25 billion in cash and stock. PANW is positioning this acquisition as the ultimate leap toward securing machine and agent identities – one of the hottest frontiers in the rapidly emerging era of AI-driven threats. The deal, expected to close in the second half of Palo Alto Networks’ fiscal 2026 with pending regulatory approval, isn’t just about shoring up next-generation identity security. It signals a seismic shift in how the biggest cybersecurity providers hope to position themselves as indispensable partners for the AI-powered enterprise. But make no mistake, this transaction goes beyond AI security market positioning; it marks a significant milestone in PANW’s broader ambition to become a comprehensive cybersecurity provider, significantly enhancing its capabilities in Identity and Access Management.
Decoding the core strengths of PANW and CyberArk
To understand why this deal matters, it’s worth breaking down the core strengths of both players:
-
- Palo Alto Networks: Traditionally, PANW has owned the threat detection and response space, with some of the world’s most advanced firewalls, endpoint detection (XDR), and comprehensive coverage of cloud, IoT, and OT environments. Products like Prisma Access have kept threat actors at bay, offering a strong SASE (Secure Access Service Edge) architecture. PANW’s growth trajectory has centered on protecting everything connecting to the enterprise – except, notably, the identities weaving through those systems
-
- CyberArk: In contrast, CyberArk is a leader of the Privileged Access Management (PAM) universe – securing passwords, credentials, and access to the most sensitive assets and data across hybrid, multi-cloud, and on-prem environments. CyberArk’s expansion into broader Identity and Access Management through strategic moves like acquiring Idaptive (for identity-as-a-service and IdP capability) and Zilla Security (for Identity Governance and Administration, or IGA) signaled their intent to cover every identity angle, from human to machine
Individually, both providers were charting impressive but different courses. PANW protected the highways of enterprise infrastructure; CyberArk owned the keys to the most sensitive doors.
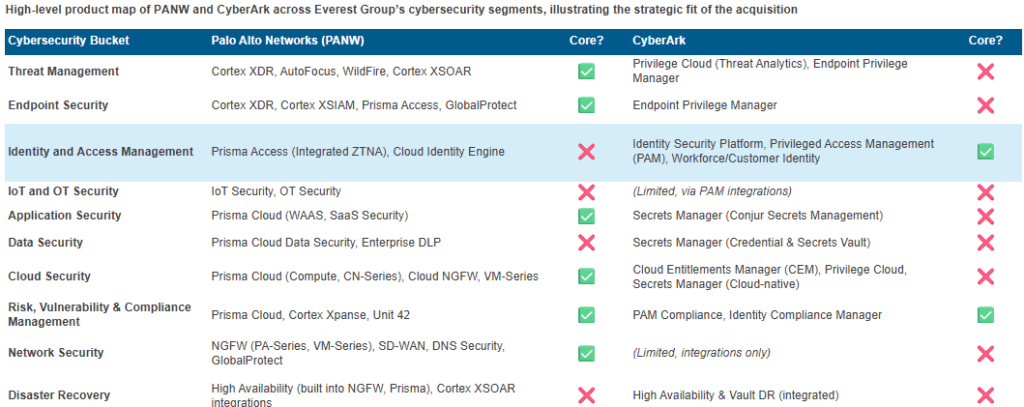
Identity – the missing puzzle piece in PANW’s end-to-end security vision
So, why does Palo Alto Networks want CyberArk? The answer: to put the most critical piece in its end-to-end security puzzle.
Consider PANW’s acquisition playbook over the past five years. Through deals like Demisto (SOAR), Expanse (attack surface management), and Bridgecrew (Infrastructure-as-Code security), PANW stitched together an industry-leading posture for protection, detection, and response across ever-expanding boundaries. Yet, the provider remained mostly outside the core Identity and Access Management space – the domain that’s increasingly seen as fundamental to modern enterprise security.
CyberArk brings precisely what PANW lacked – deep, enterprise-grade identity security. With CyberArk’s portfolio, including not just PAM but now IdP and IGA from Idaptive and Zilla, PANW can finally compete head-to-head for the “all-in-one” security platform crown. It’s a move that goes beyond SASE (Prisma Access) and traditional security perimeters, closing the gap on a zero-trust future where everything – humans, workloads, bots – must continuously prove who or what they are.
Palo Alto’s new arsenal – a real challenge to Microsoft’s security suite?
Microsoft has long enjoyed a dominant competitive edge in security and compliance, thanks to its famed E5 licensing bundle. E5’s edge comes from its tightly integrated stack that includes Entra ID (formerly Azure AD) P2 for identity, advanced conditional access and risk analytics, endpoint detection (Microsoft Defender for Endpoint), data loss prevention (Azure Information Protection), PAM, and CASB/SASE via the Defender and Purview suites. Enterprises flocked to E5 not just for security, but for the economics of bundling – getting a robust suite at a lot lesser cost compared to assembling best-of-breed tools piecemeal.
Until now, one reason PANW couldn’t truly challenge E5 was its lack of a full-fledged identity platform. With CyberArk (plus Idaptive’s Identity Provider and Zilla’s IGA) now under the PANW umbrella, that gap just closed. PANW is suddenly one of the very few providers, apart from Microsoft and perhaps Okta/Thoma Bravo portfolios, to offer all foundational Identity and Access Management capabilities (AM, PAM, and IGA) on top of its world-beating threat detection, response, and SASE stack.
This bolsters PANW’s value proposition to the massive install base of enterprises that currently look to Microsoft simply because it’s the “easy button” for security. If most E5 buyers only activate the security modules and aren’t using advanced collaboration or analytics, PANW’s new, sprawling single-provider offering could prove irresistible. Microsoft will still have unmatched channel integration and pricing power—but for the first time, there’s a credible challenger with a convincing story across the enterprise security spectrum.
How will enterprises feel this impact?
If you’re an enterprise running CyberArk or PANW, sweeping product changes won’t be immediate. Integration of two complex portfolios – especially across categories as different as infrastructure security and privileged identity management – doesn’t happen overnight. Tech integration is likely to follow a staged path once the merger is officially completed:
-
- Short term (0-6 months): No major changes to day-to-day platform experience. Backend coordination begins in sales, marketing, product, and support teams
-
- Mid-term (6-12 months): Some workflows and account relationships merge; look for “better together” bundles and cross-trained account managers. Pilot integrations and early joint solutions may emerge for flagship customers
-
- Long term (12-18+ months): Expect major advancements in platform-to-platform integration, unified identity-powered risk analytics, and perhaps a singular customer dashboard or “control tower” spanning both threat and identity. True architectural integration – beyond simple API connection – is likely 18-24 months away, but promises industry-changing potential for holistic threat and identity security
For organizations considering new investments, this move may encourage a rethink of procurement, integration patterns, or even vendor consolidation negotiations—especially if budgets are tight or simplicity is a mandate.
Redrawing the battle lines – what this means for other Identity and Access Management providers
The consolidation of PANW and CyberArk is a shot across the bow for the wider Identity and Access Management industry.
-
- A new arms race: Other leading security providers such as Microsoft, Cisco, CrowdStrike, Google, and even up-and-comers with specialized platforms will now face unprecedented pressure to either build or buy deeper Identity and Access Management capabilities. Nobody can afford to be left behind as the “one throat to choke” vision for enterprise security takes hold
-
- Squeeze on niche and standalone providers: Identity and Access Management pure-plays such as BeyondTrust, Delinea, Ping Identity, SailPoint, Okta, and Saviynt will feel the heat. They must differentiate or seek alliances quickly as customers gravitate toward unified platforms
-
- Consolidation pressure: Expect an acceleration of M&A, joint ventures, or tight partnerships as the market rallies to compete with these new security supergroups. The era of niche “best-of-breed” AM, PAM, or IGA vendors going solo against the giants could be ending
Conclusion – platform wars heat up, time to rethink partnerships
PANW’s US$25 billion acquisition of CyberArk isn’t just about riding the AI security wave. It signals the arrival of comprehensive, unified platforms where every piece of the security stack from perimeter to privilege is delivered by a single provider. For tech providers, service providers, and enterprises, this means new pressures and new opportunities:
-
- Tech providers: Must assess gaps in their portfolio and consider strategic partnerships, mergers, or accelerated roadmaps; otherwise, risk irrelevance in the age of consolidated platforms
-
- Enterprises: Should reconsider security roadmaps, supplier risk, and procurement comfort zones. With so much capability now under fewer umbrellas, single-provider dependency is a risk and opportunity in equal measure
-
- Service providers: Partner strategies need a refresh. Those with deep expertise in both PANW and CyberArk will be especially well-positioned, but agility in consulting and integration will be critical as customers navigate a rapidly transforming market
The chessboard is being reset. The only constant is the relentless push toward more integrated, identity-centric, and intelligent security for the AI-powered future.
Learn more in Everest Group’s Identity and Access Management Technology-Voice of the Customer 2025 report for a panoramic, buyer-validated view of today’s IAM technology landscape.