Blog
Separating Facts from Fiction: Debunking the Myths Around Containers | Blog

Containers have emerged as the platform of choice for developers, with more and more enterprises adopting them for the benefits they offer, including scalability to handle increased workloads, platform-independent applications, speed and efficiency, and elimination of redundancy.
Everest Group’s survey with 169 enterprise CIOs shows that more than 60% of enterprises are already leveraging containers to develop and deploy applications. The 2020 bi-annual Cloud Native Computing Foundation (CNCF) survey also estimates that the use of containers in production has increased by more than 300% since 2016.
Despite widespread adoption, however, there is significant confusion about containers in the market. In fact, many organizations are misled into adopting containers as a panacea for all IT infrastructure-related challenges. In this blog, we debunk some of the common myths about containers, clear the air on the container solution, and offer key enterprise considerations for scaling container adoption.
Common myths vs. Everest Group’s take on containers
To separate facts from fiction, we look at the common misconceptions around containers and demystify them.
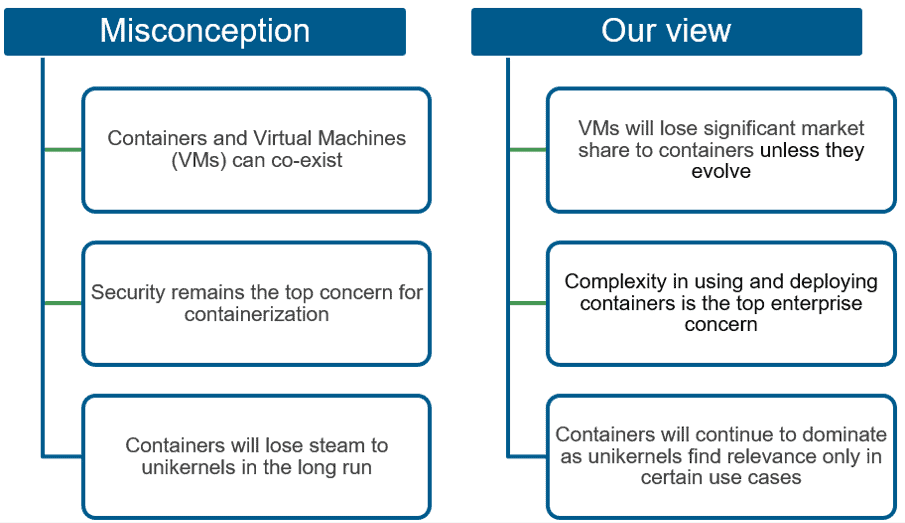
Exhibit 1: Common misconceptions about containers and our take on them
Let’s take a closer look at these myths.
Myth 1: Containers do not pose a threat to Virtual Machines (VMs); the two can co-exist
Most enterprises today are leveraging containers in VMs to provide the latter’s robust security for running containerized workloads. Virtualization technology vendors such as VMware also support the view that containers and VMs will coexist, and enterprises stand to maximize their benefits by leveraging containers within VMs.
Our view: VMs will lose significant market share to containers in the long run
Currently, enterprises are trading off between performance and security by deploying containers on top of VMs. The containers-within-VM model enhances the security of container deployment but loses some performance benefits. However, in the long run, as container technology matures and becomes inherently secure, the containers-within-VM model will be inefficient and, in fact, reduce utilization and efficiency.
Myth 2: Security is the top enterprise concern in containerization
In contrast to VMs, containers share a common host OS, which can more easily expose the entire system to security threats. These threats can be easily transferred across containers through a shared OS. The 2017 CNCF survey of 550 respondents cited security as the top challenge while deploying containers.
Our view: Complexity in using and deploying containers is the top enterprise concern
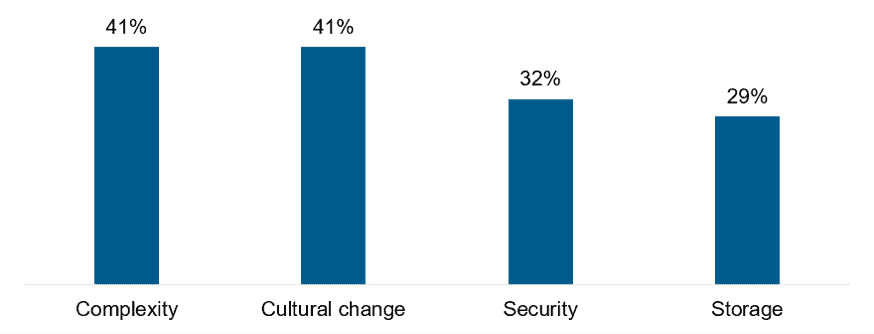
Container security remains a vital enterprise priority, but continued investments in the container security space have ensured that enterprises need to be cautious with container security, not concerned. In the 2020 CNCF survey, enterprise concerns around security declined to 32% from 38% in 2019. This increased confidence can be attributed to investments made by Enterprise Container Platforms (ECPs) such as Red Hat and Docker, as well as niche players in this space. At the same time, containers’ scalable architecture means that enterprises can rapidly spin up new containers, creating a complex IT estate that can be difficult to manage.
Exhibit 2 indicates the top enterprise concerns in container implementation.
Exhibit 2: Top enterprise concerns in container implementation
Myth 3: Containers will lose steam in the long run and be replaced by unikernels
Unlike containers, which share an OS kernel across all the running containers, unikernels contain their own dedicated single-purpose kernel. As a result, unikernels boast of a single lightweight image, which provides limited surface area for attack, making them more secure.
Our view: Containers will continue to dominate as unikernels find relevance only in certain use cases
Unikernels came into prominence when Docker acquired Unikernels Systems in 2016 with the goal of democratizing unikernel technology; however, the technology is still not considered enterprise-grade by most large organizations. In addition to technology-specific challenges, such as inefficient debugging and streamlining builds, unikernels suffer from more broad-based challenges, such as the lack of a mature technology ecosystem and enterprise traction. Thus, while unikernels will find use in edge and IoT devices, where processing power and storage are in short supply, containers will continue their strong run and more expansive spread by helping enterprises transform monolithic applications and bringing agility to businesses.
Enterprise considerations for scaling container adoption
Given the benefits that they offer and a promising outlook, containers seem to be here to stay. At the same time, enterprises need to be mindful that capturing breakthrough value from containers is not about technology considerations alone. Organizations need to undertake significant changes to move beyond isolated benefits in a dev/test environment to strategic benefits in the production environment. They also need to devise a holistic adoption roadmap/strategy for containers that aligns with their specific business objectives, enterprise design considerations, and technology and operations maturity levels.
There are several key considerations for enterprises scaling up container adoption:
- Take a phased adoption approach: Enterprises would benefit from testing the waters without having to make significant up-front investments. They can start by leveraging containers in a test/dev environment and scale up by containerizing best-suited workloads in the staging and production environments.
- Identify your business objectives: Needless to say, container strategies should be aligned with business requirements. Once the requirements are established, enterprises can determine the type of container model, talent requirements, and investments required.
- Prioritize security and governance: Embedded security has become an integral issue for enterprises, and it should also be aligned to the container strategy. Given that new containers are created and destroyed in minutes, or even seconds, enterprises need real-time monitoring and threat detection for containers.
- Define the right value metrics: Identifying the right set of value metrics is crucial to measuring the success of the container initiative, as well as identifying shortcomings for course correction. Enterprises need to choose relevant value metrics in line with their business objectives.
- Drive effective change management: A successful container strategy requires an organizational mandate. It is vital to identify enterprise champions who can evangelize and continually govern progress. Enterprises also need to invest in building the right skill set to drive container implementation.
If you have more questions about containers or are trying to figure whether the solution would benefit your enterprise, please write to us at [email protected] and [email protected].