Blog
Securing the Front Door: How Transforming Service Desk Is Foundational to Zero-trust

In an era where zero-trust dominates enterprise security playbooks with talks about hardened endpoints, Multi Factor Authentication (MFA) rollouts, and behavioural anomaly detection, service desk remains surprisingly exposed. Amid all this noise of layered security investments, a simple phone call still breaks the chain.
Reach out to discuss this topic in depth.
Case in point: In August 2023, Clorox became the latest victim. Attackers allegedly tricked a Level 1 service desk agent into resetting credentials and bypassing MFA bringing operations to a halt and triggering a US$380 million lawsuit filed in July 2025. However, Clorox is not an outlier it is just the latest reminder that the service desk remains one of the softest spots in the zero-trust stack.
Consider the recent lineup of service desk breaches:
-
- MGM resorts (2023): ALPHV/BlackCat spent ten minutes on LinkedIn, phoned the service desk, and shut down hotels and casinos for ten days
- Caesars entertainment (2023): The same gang socially engineered service desk staff, exfiltrated loyalty data, and allegedly collected a $30 million ransom
- Kojima Industries (2022): A supplier-desk breach halted Kanban Information Technology (IT) and idled 14 plants, leading to a loss of 13 000 cars in a day
The lesson: Service desks are not just support channels; they’re the soft underbelly for enterprise breaches. Zero-trust fails if the first hello isn’t protected.
The help desk breach map
Despite security spend elsewhere, service desks often rely on fragile processes, skipped checks, broad access, weak ID proofing, and limited logging. These gaps make Level 0/1 a high-risk entry point, where a single lapse can undo downstream controls.
The below table shows how such failures have led to major breaches:
Exhibit 1: Cases of help desk exploits across the industry
| Breach trigger | Breach (year) | Root cause |
| Human lapse | Marks & Spencer ’25 | Agent rushed, skipped checks |
| Excess privilege | Storm-1811 Quick Assist ’24 | Screen-share opened domain-admin rights |
| Logging gaps | Okta Support ’23 → scope revised ’24 | Audit trail too narrow to trace impact |
| Proofing (ID) | Clorox vs Cognizant ’23/’25 | Voice accepted as identity |
These controls were built assuming everything goes right. Zero-trust, by definition, must hold even when everything goes wrong. However, a single lapse in human judgment and the chain snaps.
Redesigning the service desk: Automate trust from the first touch
True zero-trust starts before an attacker ever reaches the console. That means a modern service desk should work in a closed-loop defence where artificial intelligence (AI) and humans reinforce each other.
Exhibit 2 showcase how AI guardrails + human judgement = Secure service desk
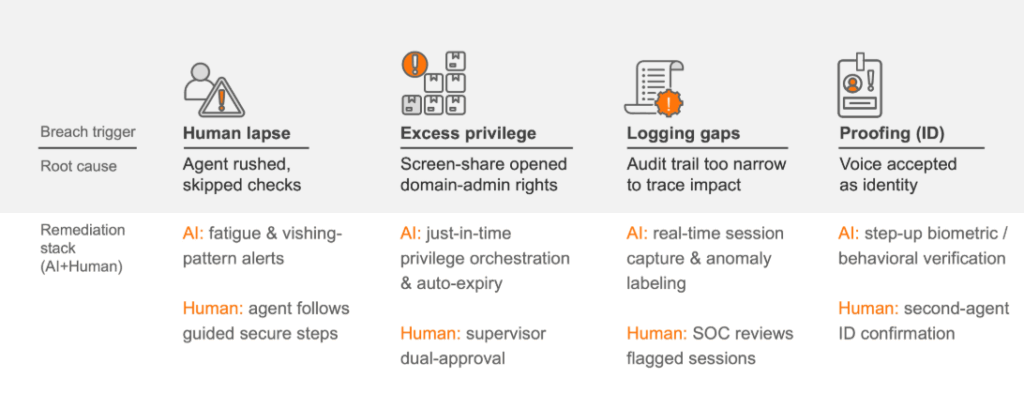
Building blocks of a secure service desk
-
- Adaptive identity proofing: Verify users based on contextual risk not just static credentials, before executing any sensitive request.
- Dual-authorization protocols: No single agent should have the ability to override MFA or escalate access alone.
- Just-in-time entitlements: Grant temporary, purpose-bound privileges that auto-expire.
- Immutable audit trails: Stream all service desk activity into a central Security Information and Event Management (SIEM) to enable traceability and real-time anomaly detection.
- AI-human feedback loops: Use telemetry to retrain models and improve workflows, so defences evolve with attack patterns.
Regulatory tailwinds are also catching up
The regulatory climate is catching up from guidance to enforcement, with new mandates placing direct accountability on internal support functions including the service desk
-
- NIST SP 800-207: Mandates uniform policy enforcement across user tiers including internal actors like help desk personnel
- EU NIS2 Directive (2025): Expected to tighten service desk controls with requirements for override logging, risk scoring, and escalation workflows
Non-compliance won’t just mean fines it will mean boardroom accountability.
What enterprise leaders must do now
To close the most human vulnerability in the security stack, enterprise Chief Information Security Officers (CISOs) and Chief Operating Officers (COOs) should:
-
- Push zero-trust enforcement to Level 0: Embed AI-driven context-aware identity verification into service-desk workflows
- Kill one-click overrides: Mandate dual approvals for high-risk actions like MFA resets, access escalation, or device provisioning
- Instrument full-stack observability: Log agent actions, reasons, and decisions in real time, feeding an observability tower for forensic analysis and pattern detection
- Deploy Agentic AI agents: Use autonomous agents to monitor risk scores, enforce escalation protocols, and trigger real-time interventions
- Elevate the desk to a control tower: Track Key Performance Indicators (KPIs) for breach resistance, verification accuracy, and retraining cadence
- Simulate, stress, and improve: Run regular social engineering drills to test frontline response and adapt quickly. Use each attempt to fine-tune controls, update playbooks, and evolve defences, continuous improvement is the only defence against evolving threats
Trust is earned at the first hello
Enterprises have invested heavily in digital perimeter defences, but attackers aren’t breaking down firewalls anymore; they’re simply walking through the front door.
As social engineering and AI-driven impersonation accelerates, service desks must evolve from vulnerability to vanguard in the enterprise security posture.
To help benchmark your service desk’s zero-trust readiness, or discuss your digital workplace journey reach out to: [email protected] and [email protected]