Blog
Taking a Value Chain-led View to Secure Healthcare Enterprises | Blog

Between 2018 and 2019, the US healthcare industry experienced a five-fold increase in patient data breaches, with hacking accounting for more than 88 percent of them. More than half of the targeted entities were healthcare providers, primarily due to inadequate investments in cybersecurity and the negligence of unsuspecting employees.
Patient data is sacrosanct for the healthcare industry given its highly sensitive nature. In fact, patient Electronic Health Records (EHRs) are priced 10 times higher than credit card information on the dark web. Given that healthcare data is a lucrative target for cyber attackers, healthcare CXOs need a guided approach to secure their patients and enterprises against cybersecurity threats.
A value chain-led view of cybersecurity
Healthcare enterprises are becoming increasingly vulnerable to attacks as patient-centric care takes center stage and care delivery models such as mHealth and remote monitoring become commonplace. So, they must identify their crown jewels – patient data, care delivery applications, and medical devices, among others – across the value chain and allocate their cybersecurity investments accordingly. To do so, they need to contextualize threat intelligence, understand attackers’ behavior and intent, and make appropriate investments in cybersecurity to increase preparedness and reduce response time in the event of a breach.
Stress-testing the value chain-led view
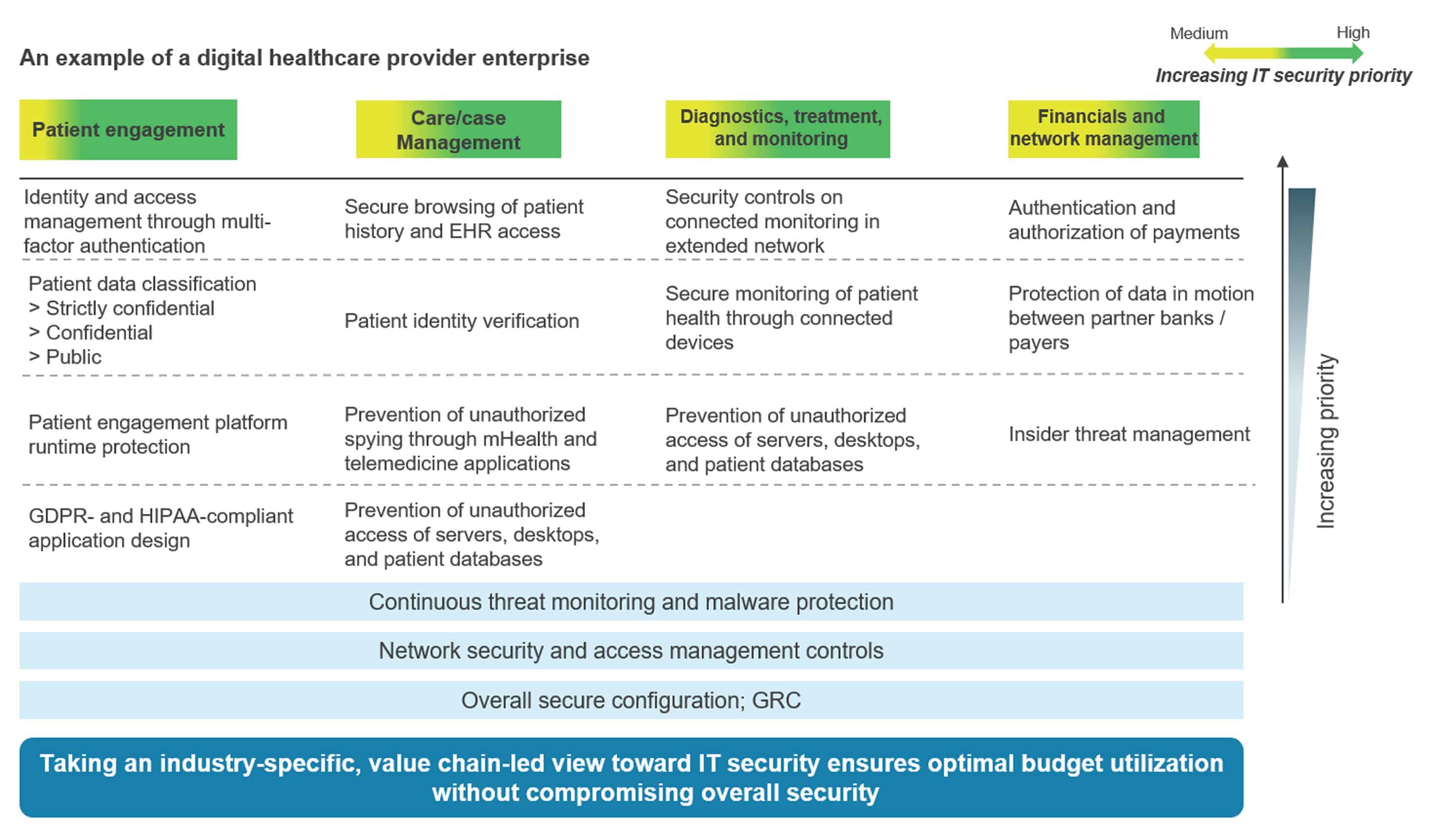
To hack-proof their estates, healthcare enterprises need to adopt a value chain-led view to identify and alleviate cybersecurity concerns across four areas:
- Patient engagement: Patient care starts as soon as a patient is made aware of a health condition. To prevent any patient data leaks, healthcare applications must be HIPAA-compliant, designed with patient privacy at the center, and have strong identity and access management controls.
- Care/case management: The primary activities in care/case management are appointment scheduling, remote consultations, and mHealth application use, for which physicians need access to sensitive EHR data. It’s important to incorporate patient identity verification and data security layers for EHR access, as well as to build in network and endpoint security protocols to protect EHRs and devices connected to them.
- Diagnostics, treatment, and monitoring: As medical devices increasingly connect to the provider network, malware attacks aimed at halting care operations threaten to disrupt hospital functioning. Healthcare enterprises can strengthen their endpoints by adopting malware protection, endpoint detection and response solutions, and device management software. Additionally, providers need to prevent unauthorized access to their systems.
- Financials and network management: Providers should also invest in data and network security to make sure all patients’, payers’, and banks’ financial transactions are safe and secure.
Here’s an example of how a healthcare provider can prioritize its IT security investments in accordance with its business priorities by taking a value-chain view.
Setting the wheels in motion
Once healthcare enterprises have identified what to do to bolster security across the value chain, they need to think about how to do it. We recommend a three-phased approach:
- Prioritize: Enterprises need to prioritize their investments and chart out a strategic and technical implementation roadmap. Having a cyber architecture in place, along with a future security plan, will aid implementation.
- Evangelize: Once implementation begins, providers should address internal risks and change management by combining a consultative approach with a sharp focus on managed services. They should ensure that all business units across the value chain are involved for a harmonized security view.
- Protect at scale: They should also invest in talent, short-term detection, and long-term threat investigation capabilities across the value chain, as well as solutions contextualized for threat management.
A real-life example of the value chain-led approach in action
US-based Trinity Health adopted an enterprise-wide data security strategy in the aftermath of the WannaCry ransomware attack in 2017. It implemented an asset management plan to govern its connected devices and networks to improve its response to adverse events. It also instituted an event response team to isolate, contain, and deploy patches when threats were identified. Realizing that its employees could also be vulnerable targets, Trinity Health initiated exercises to help them recognize and respond to cybersecurity threats. And that’s not all; it also leveraged the National Institute of Standards and Technology (NIST) Cybersecurity Framework to redesign its procurement process, technology and security assessments, and supplier evaluation responsibilities to recover in case of actual emergencies.
In an industry committed to digital transformation and increasingly embracing patient-centric care, healthcare providers must devise a well-thought-out cybersecurity strategy to protect their crown jewels across the value chain. This is the only way they’ll retain patients’ trust, drive brand value, and ensure better outcomes for all stakeholders involved.