Demystifying Data Security - A Comprehensive Guide to Data Security | Blog

Data security became a critical focus area for enterprises in 2024 due to numerous factors, with the increasing adoption of artificial intelligence (AI) leading the charge.
According to the 2025 World Economic Forum’s Report1, 20% of enterprises are most concerned about data leaks linked to Generative AI (gen AI) adoption. This places data leaks as the second-highest concern, trailing only adversarial capabilities such as phishing and deep fakes.
To fully grasp this growing concern, it’s essential to explore the fundamentals of data security and its significance in today’s digital landscape, which is what our analysts have done in this latest blog.
Reach out to discuss this topic in depth.
Understanding data security
Data security refers to the practice of protecting data from unauthorized access, theft, or corruption throughout its lifecycle, whether it resides on-premises, in the cloud, or within hybrid environments.
It encompasses a range of measures, from physical safeguards to advanced digital solutions. For this blog, we have focused on the digital aspects of data security.
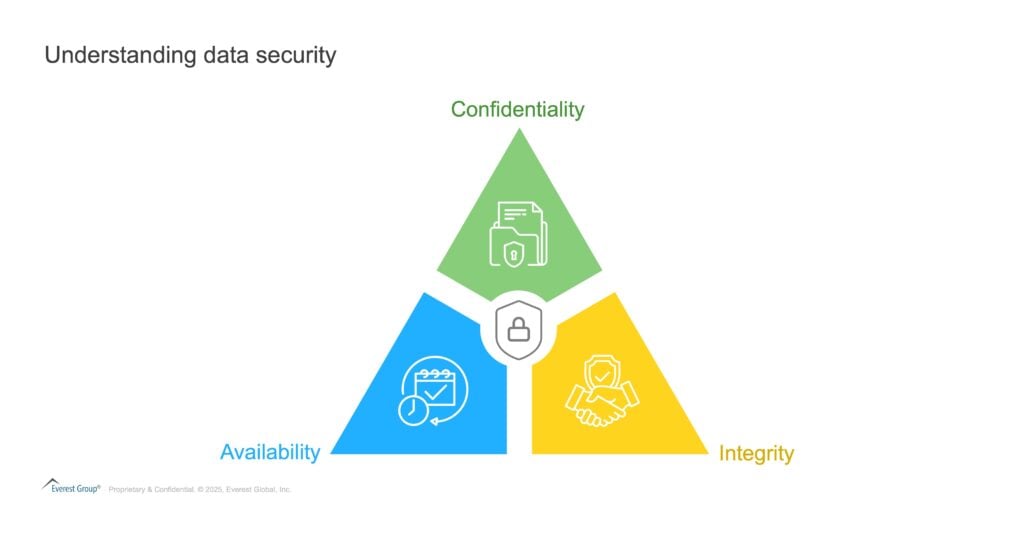
A widely used framework to define data security is the Central Intelligence Agency (CIA) Triad2, which comprises three core principles:
-
- Confidentiality – preserving authorized restrictions on information access and disclosure, including means for protecting personal privacy and proprietary information
-
- Integrity – guarding against improper information modification or destruction and ensuring information non-repudiation and authenticity
-
- Availability – ensuring timely and reliable access to and use of information
These principles form the foundation of a robust data security strategy and guide enterprises in securing their sensitive information. With the basics of the CIA Triad established, it’s also critical to differentiate data security from a closely related but distinct concept—data privacy.
Data security vs. data privacy
Building on the CIA Triad, it is essential to distinguish between data security and data privacy, as these concepts often overlap but serve distinct purposes. While data security focuses on protecting data from external threats, data privacy addresses how data is handled and shared within organizations. Here’s a simple comparison:
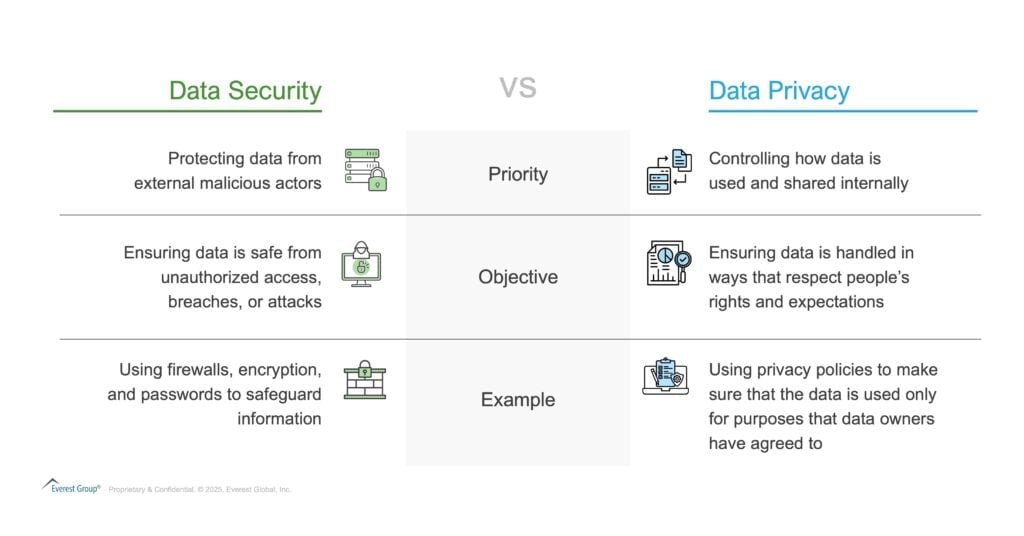
In essence, data security focuses on keeping data safe, while data privacy ensures its ethical and responsible usage. Understanding these distinctions sets the stage for examining the key drivers and challenges shaping the data security landscape.
Drivers and challenges of data security
With a clear understanding of what data security entails, it’s important to examine the factors driving its adoption and the challenges that hinder implementation. This helps contextualize why data security has become a pressing priority.
Key drivers
-
- Gen AI adoption – The growing use of gen AI heightens concerns about protecting sensitive data during training and operations. Enterprises are prioritizing measures to prevent intellectual property leaks, unauthorized access, and accidental exposure
-
- Increasing cyber threats – Cyberattacks, including ransomware, phishing, and Advanced Persistent Threats (APTs), are becoming more sophisticated. Robust data security is essential to safeguard sensitive information and maintaining business continuity
-
- Regulatory compliance pressure – Stringent regulations like General Data Protection Regulation (GDPR), EU AI Act, National Institution of Standards and Technology Artificial Intelligence Risk Management Framework (NIST AI RMF), California Consumer Privacy Act CCPA, and India’s Digital Personal Data Protection (DPDP) Act compel organizations to adopt stringent security protocols. Compliance builds trust and ensures adherence to legal obligations
Major challenges
-
- Complex technology landscape – Integrating diverse security solutions across hybrid and multi-cloud environments is challenging, leading to vulnerabilities
-
- Evolving threat vectors – Cybercriminals continually refine tactics, making it difficult for organizations to stay ahead without agile security frameworks
-
- Resource and budget constraints – Many organizations struggle to allocate sufficient budgets and skilled personnel, limiting their ability to implement effective security measures
With these drivers and challenges in mind, understanding the types of data security solutions available becomes crucial to overcoming these obstacles effectively.
Types of data security solutions and technologies
For successful implementation of data security, organizations must rely on a structured approach rooted in the CIA Triad. This ensures that all aspects of confidentiality, integrity, and availability are addressed using the right solutions and tools.
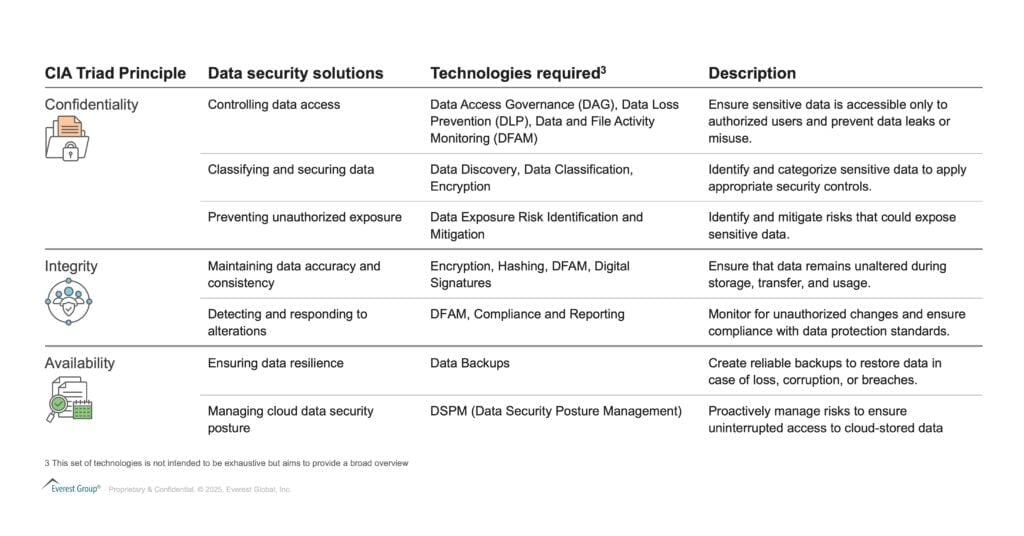
This structured approach equips enterprises to secure data effectively while addressing unique organizational needs. Next, we explore the pivotal role of service providers in driving data security initiatives.
What should providers do about data security?
Recognizing the complexities outlined above, providers play a critical role in supporting enterprises as they navigate the evolving data security landscape. Here are actionable strategies for providers:
-
- Collaboration with specialized security providers – Enterprises expect service providers to forge strategic partnerships with industry-leading encryption, Data Security Posture Management (DSPM), Data Loss Protection (DLP), and AI-security experts. The complexity of today’s threats demands a robust ecosystem of specialized tools and technologies to ensure comprehensive protection and continuous innovation
-
- Tailored and scalable security solutions – Enterprises demand data security solutions that can adapt to different organizational sizes and industry requirements. From lightweight, cost-effective defenses for smaller entities to advanced, multi-tiered frameworks for large enterprises, providers must deliver a scalable approach that addresses diverse risk profiles
-
- Proactive compliance and regulatory alignment – Organizations expect service providers to stay ahead of global and local regulations, offering proactive advisory services, automated compliance reporting, and real-time monitoring. By anticipating and adapting to legal requirements, they position themselves as trusted partners who ensure organization’s uninterrupted compliance
-
- End-to-end coverage across the CIA triad – Enterprises look to technology providers to deliver integrated solutions that address all facets of the CIA triad. This requires both established capabilities—like encryption and data loss prevention—and emerging innovations, such as DSPM, to cover the full spectrum of modern data security demands
-
- AI-driven innovation for advanced threat detection – Enterprises expect technology providers to harness AI to transform data security. From automated risk assessments and predictive threat intelligence to streamlined incident response, AI-enabled solutions must now offer faster, smarter, and more adaptive defenses that help us outpace evolving cyber risks
What we believe is next…
As enterprises navigate the complexities of data security, it’s clear that protecting digital assets is no longer optional—it’s a necessity. The adoption of AI, increasing cyber threats, and regulatory pressures are now reshaping the landscape, demanding innovative and comprehensive solutions. By leveraging advanced tools, focusing on education, and building strong ecosystems, service providers can now lead the way in securing the future of digital information!
If you found this blog interesting, check out our MXDR: A Revolutionary And Comprehensive Solution Transforming Cybersecurity Detection And Response | Blog – Everest Group blog, which delves deeper into another topic regarding data and cybersecurity.
To discuss data security in more depth with our team, please contact Kumar Avijit ([email protected]) and Arjun Chauhan ([email protected]).
1. WEF Report on Cybersecurity Outlook 2024
2. NIST 1800-26
3. This set of technologies is not intended to be exhaustive but aims to provide a broad overview