As the immersive experience landscape evolves from its initial stages to a fully realized state, it promises to transform both consumer and enterprise digital experiences. Despite its early development, enterprises are increasingly recognizing its value and are poised to increase investments in this field. This market is driven by the surging consumer demand for immersive and captivating experiences, presenting numerous opportunities for enterprises across various sectors. The potential applications of immersive technology span diverse areas, such as immersive marketing, enhanced customer experiences, improved employee training, and the facilitation of live virtual events and digital asset trading.
Advances in Virtual Reality (VR), Augmented Reality (AR), and Mixed Reality (MR) technologies are propelling this growth, offering users and enterprises immersive content experiences. The integration of immersive technologies across sectors such as Banking, Financial Services, and Insurance, manufacturing, retail, education, gaming, healthcare, hi-tech, and entertainment is reshaping consumer behaviors and creating new opportunities for engaging experiences. The expanding market is further fueled by rising investment in immersive technology and Web 3.0, indicating a promising future for immersive experience services across industries.
Contents:
In this report, we:
Scope:
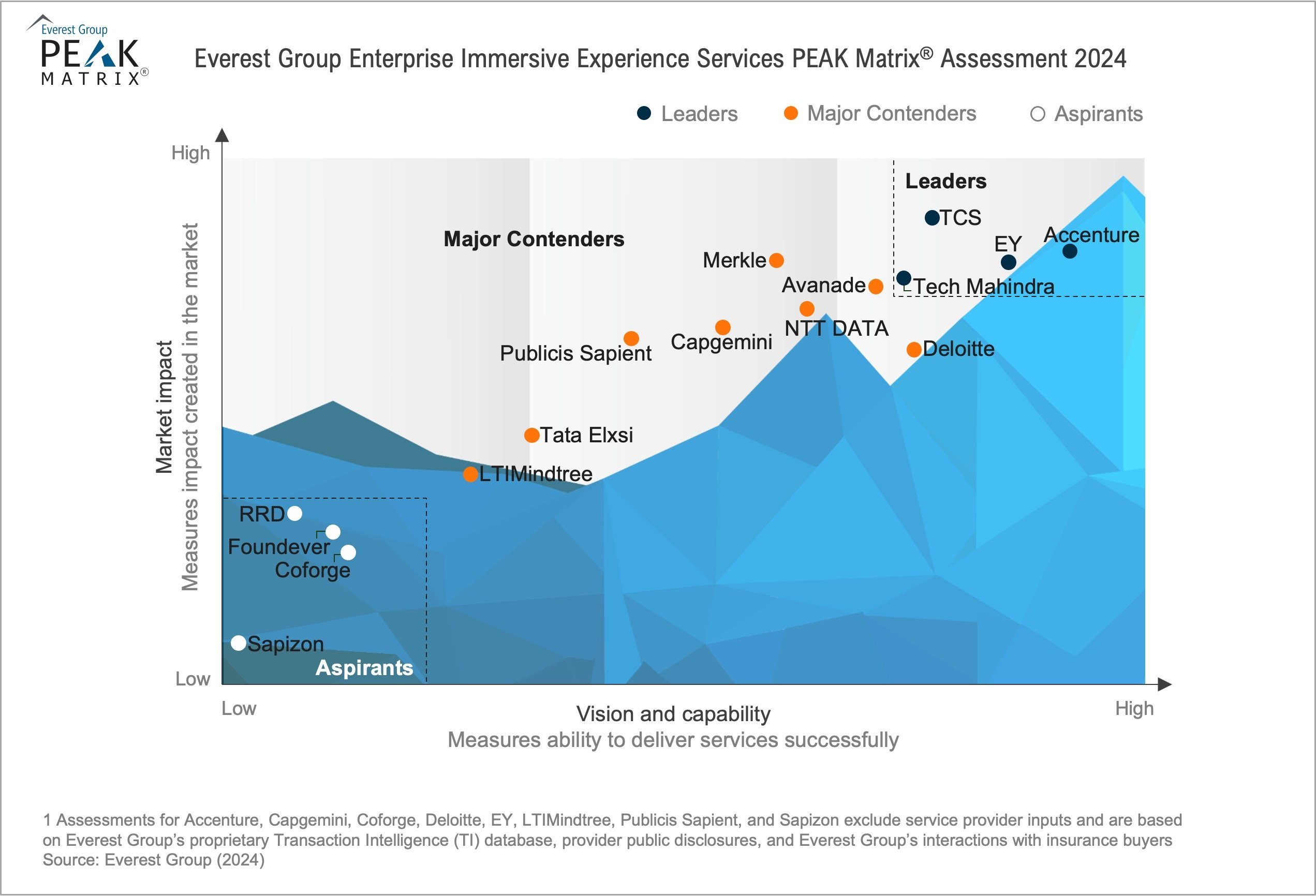
The PEAK Matrix® provides an objective, data-driven assessment of service and technology providers based on their overall capability and market impact across different global services markets, classifying them into three categories: Leaders, Major Contenders, and Aspirants.
Thierry Delaporte was announced as the CEO and MD of Wipro in July 2020. Since 2020, the value of the company’s stock and market capitalization grew by 2.5X. But the Frenchman could not complete his five-year tenure.
Peter Bendor-Samuel, CEO of Everest Group, puts it, “As a European, it was difficult to win the hearts and minds of a traditional Indian IT services firm and this undoubtedly also contributed to flagging morale.”
Wipro has a new CEO. Srinivas (Srini) Pallia was named chief executive and managing director with immediate effect on April 6, according to a press release from India’s fourth-biggest IT services company.
Pallia will replace Thierry Delaporte, ending Wipro’s four-year experiment with a foreign CEO. “It is very hard for a non-Indian to run a large Indian firm,” Peter Bendor-Samuel, CEO of Everest Group, says. And the macroeconomic conditions that he had no control over made Delaporte’s job that much harder.
HCL Technologies Ltd is projected to top the charts in revenue growth and profitability among IT services companies in FY24.
Chirajeet Sengupta, Managing Partner at Everest Group, concurred, adding there have been “no signs of recovery that the industry has seen through the last three months of FY24.”
Post-quantum cryptography (PQC) has become essential for enterprises to protect against future quantum-enabled attacks and secure digital assets and sensitive data. Read on to discover providers’ crucial role in preparing enterprises for PQC. Reach out to explore this topic further.
As discussed in our previous blog, the emergence of quantum computing poses a significant threat to current public key cryptographic methods. When run on quantum computers – or more specifically, Cryptographically Relevant Quantum Computers (CRQCs) – some algorithms such as Shor’s can potentially break widely used methods like RSA, DSA, ECDSA, EdDSA, and DHKE, among others.
The advancement of quantum computers can seriously threaten data security and privacy for various enterprises, affecting fundamental principles such as confidentiality, integrity, and authentication. This makes it essential to reassess the security of these cryptographic methods.
The early and widespread use of quantum computers could wreak havoc, enabling new advanced cyberattacks that are impossible using classical computers. Post-quantum cryptography (PQC) is the solution to this problem. Let’s explore this further.
In the quantum computing era, PQC is vital in ensuring the long-term security of digital communication and data protection. PQC focuses on researching and adopting cryptographic algorithms that are ready for this era.
These algorithms are designed to be secure against both quantum and classical computers. Furthermore, they are expected to be deployable and integrable without significant modifications to current protocols and networks.
With extensive ongoing research in this field, researchers have proposed several mathematical schemes that meet the requirements for being potential candidates for quantum-safe cryptographic algorithms. These include lattice-based, multivariate polynomial, code-based, hash-based, and isogeny-based cryptography.
The U.S. Department of Commerce’s National Institute of Standards and Technology (NIST) launched a program in 2016 to create standardized quantum-safe cryptographic algorithms.
After a rigorous six-year evaluation involving global experts, it announced four finalists for quantum-safe cryptographic standards. The following algorithms selected by NIST address general encryption and digital signatures that are crucial for securing data exchanges and identity authentication:
| PQC algorithm | Cryptographic scheme | Purpose |
| CRYSTALS-Kyber | Lattice-based cryptography | Key encapsulation method (KEM) |
| CRYSTALS-Dilithium | Lattice-based cryptography | Digital signature |
| FALCON | Lattice-based cryptography | Small digital signature |
| SPHINCS+ | Hash-based cryptography | Digital signature |
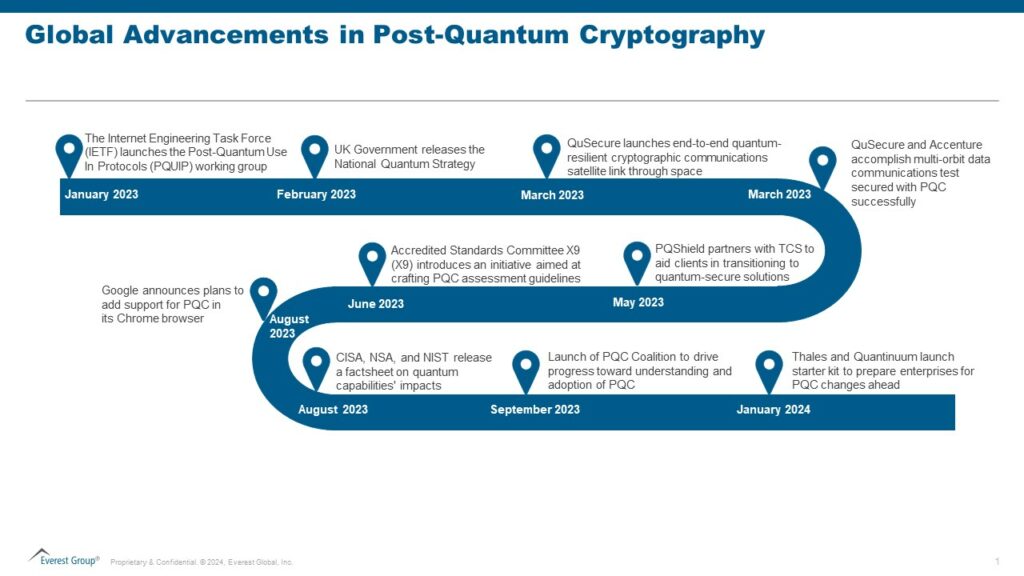
Several other developments related to PQC have occurred recently. The notable ones are highlighted below:
The complexity of cryptographic fields makes it difficult for enterprises to navigate data security. With numerous algorithms, protocols, and standards, enterprises often struggle to understand and implement robust cryptographic solutions.
Enterprises may encounter several common cryptographic pitfalls, including:
Enterprise considerations for embracing PQC
Considering the current challenges with cryptography, enterprises would face far more significant difficulties if they do not strategically plan for PQC. To prevent this, cybersecurity leaders globally must proactively prepare and initiate early plans to migrate to post-quantum cryptographic standards.
Taking a proactive stance is crucial since transitioning to new quantum-safe algorithms will be discontinuous, considering the inherent disparities in key size, error-handling properties, and other complexities.
Hence, enterprises should give themselves enough time to start small, experiment, learn from positive impacts and challenges, and explore ways to reduce technology transition costs.
Staying abreast of advancements in quantum computing and quantum-safe solutions is paramount. Enterprises must establish a comprehensive quantum readiness roadmap following these five steps:
Streamline the current cryptographic infrastructure: Enterprises can initiate modernization efforts by streamlining their current cryptographic infrastructure, including consolidating or replacing vendors to enable a managed migration process. The CFO should collaborate with other executives to prioritize PQC investments based on the risk appetite and strategic objectives and adopt a fully crypto-agile approach. Establishing a governance structure with clearly defined roles and responsibilities to adopt PQC effectively is also recommended.
There is an ongoing debate over some adversaries already gathering encrypted foreign communications, anticipating the future ability of quantum computers to decrypt such systems, and aiming to extract valuable secrets from the data collected. This threat, known as “harvest now, decrypt later,” highlights the urgency of making cryptographic changes rather than waiting.
As quantum computing advances, the demand for comprehensive quantum-resistant cryptographic solutions will only increase, favoring a ripe market for cybersecurity service providers to capitalize on.
PQC offers a significant opportunity for providers to position themselves as vital partners in ensuring the security and resilience of enterprises’ digital assets against the evolving quantum computing threats.
Leaders may need help understanding the advanced mathematical concepts and algorithms involved in PQC. The complexity of these cryptographic methods may need to be clarified for enterprises trying to grasp the intricacies of quantum-resistant solutions.
With all the latest discussions about quantum computers, service providers should take this time to develop a perspective on how PQC would impact enterprises from various industry verticals.
Providers should play an educational role, creating awareness about the risks posed by quantum computing and guiding enterprises on the importance of proactively transitioning to quantum-resistant solutions.
Service providers should develop strategies to hire, train, and upskill talent in PQC and quantum computing concepts. Additionally, they can invest in R&D initiatives to explore new approaches and solutions in the PQC field. By collaborating with relevant technology vendors, research institutions, and other organizations paving the way for PQC, service providers can foster innovation and help their clients stay at the forefront of technological advancements.
Cybersecurity service providers can offer specialized consultation and assessment services to help enterprises evaluate and inventory their current cryptographic infrastructure, prioritize components based on risk, identify vulnerabilities to quantum attacks, and recommend appropriate post-quantum cryptographic solutions.
Moreover, they can engage with enterprises on initial levels to develop comprehensive strategies for implementing and managing these solutions effectively, ensuring seamless integration with existing security frameworks and compatibility with legacy systems.
Service providers should prioritize PQC to address the threat quantum computing poses to traditional cryptographic systems. By embracing PQC, service providers can safeguard their clients’ data and infrastructure against potential quantum attacks.
Additionally, they can explore new use cases for PQC to unlock innovative solutions and stay ahead of the curve in the rapidly evolving quantum landscape. These new use cases may include:
PQC is no longer a theoretical concept but a reality. Multiple applications of PQC have emerged. In their latest release, OpenSSL has fully enabled PQC for digital signatures and fundamental establishment mechanisms. The Signal Protocol, an essential constituent of Signal, Google RCS, and WhatsApp messengers, has also announced support for the PQXDH protocol, becoming the first to introduce PQC for the initial key establishment. Apple has introduced a fresh encryption protocol named PQ3 for iMessage, offering advanced post-quantum security measures for instant messaging.
PQC is rapidly gaining traction for quantum-safe digital signatures, encryption, and fundamental exchange mechanisms. Its widespread adoption seems inevitable as the risks of quantum supremacy proliferate.
The standardized algorithms aren’t battle-tested yet, and exploitable weaknesses could be uncovered, leading to adjustments in their functioning or the development of entirely new algorithms.
We anticipate PQC becoming the cornerstone of cybersecurity strategies in the coming years. Moreover, the security standards are expected to recommend or mandate PQC.
PQC has become a crucial element of enterprise security, safeguarding against quantum-enabled attacks and ensuring the integrity and confidentiality of sensitive data.
Enterprises must start planning to migrate from a secure lock to an unbreakable vault: post-quantum cryptography! Service providers play a crucial role in guiding and supporting enterprises every step of the way.
To discuss post-quantum cryptography further, please contact Prabhjyot Kaur, Kumar Avijit, and Ronak Doshi.
Everest Group’s latest Forces & Foresight research revealed that the IT services industry is on the brink of a gradual recovery in 2024 after enduring the impacts of the 2008 global financial crisis and the COVID-19 pandemic.
According to Everest Group Vice President Prashant Shukla, the path to recovery this time around is expected to be more measured — unlike the sharp rebounds observed after previous downturns — and influenced by a mix of stabilizing factors and emerging demand in specific sectors.
Welcome to our monthly India IT services talent demand index. We are excited to bring you this comprehensive analysis, powered by Talent Genius™, our AI-powered insights platform purpose-built to guide IT and Business Process Services location and workforce decisions. To gain a deeper understanding of the capabilities of Talent Genius and learn how to book a demo, watch this quick 2-minute video, Introducing Talent Genius™.
Here is our in-depth analyses of the India IT services industry demand:
Demand for IT services in India hit a 17-month low due to declining spending and clients postponing projects. As a result, most Indian IT service providers are reexamining revenue and hiring forecasts. The overall demand across service providers decreased by 28% from last month and 11% from the previous year.
Many service providers slowed hiring, realizing they posted jobs too early and hired ahead of the demand. Service providers are now focusing on improving employee utilization rates and do not anticipate the job requirements returning to the original levels anytime soon. Demand for IT services also declined by a notable 20 percent across enterprises from November.
Overall, the second half was slower than the first half, with demand falling by 7% for service providers and 4% for enterprises. Service providers were impacted more as enterprises cut discretionary spending and insourced some work.
At the city level, demand for employees declined consistently across tier 1, 2, and 3 cities. After peaking in November, the workforce requirements in Hyderabad and Chennai fell significantly by 32% this month.
Demand hit its lowest point of the year across all segments. Despite relatively stable employment over the last few months, retail and healthcare had the biggest drop at 35%. While it is uncertain if this is the bottom, a full recovery is not expected in the near future.
IT services demand in India increased by 9% month-on-month and 5% year-on-year. Demand for IT application data management (ADM) grew 9.5%, and IT infrastructure increased 5 percent compared to the prior month. However, the surge is expected to be temporary because macroeconomic conditions pushed IT project timelines ahead for most companies.
Talent demand increased more in tier 2/3 cities than tier 1 cities, indicating that enterprises are increasingly confident in hiring outside tier 1 cities to gain a labor cost arbitrage advantage.
The number of available positions increased in all tier 1 cities, except Kolkata, where the job postings fell for the second consecutive month. Since the prior month, job openings increased 18% in Hyderabad and 14% in Chennai, representing the highest month-on-month increase.
Among tier 2/3 cities, Jaipur recorded one of the highest month-on-month increases in open positions at 34%. All the other cities experienced increased monthly postings – except for Chandigarh and Thiruvananthapuram.
IT services demand increased across all industry segments, with service providers and manufacturing demonstrating the most strength, up 5% from October.
Demand fluctuates more for service providers than other enterprises. As clients cut back on outsourcing spending, the talent need from service providers is expected to decrease in the coming months.
The demand for IT services in India declined by 9% from last month but increased by 5% year-on-year, with significant variation over the past few months. Despite the shifts, demand remains near the same level as May 2023, when IT services demand increased after being at its 12-month lowest the prior month.
Tier 2/3 cities continued to be more attractive for companies seeking employees. Hyderabad and Kolkata had the biggest monthly drop in talent demand among tier 1 cities at 15% and 12%, respectively. Employee talent needs remained the most stable in Pune, with only a 5% drop compared to the previous month.
Although demand for most roles declined, help desk engineer, data analyst, and business analyst roles continued to increase by about 5% monthly. Only the retail segment maintained net positive month-on-month growth rates at about 7%. Cyclical commodities and service providers declined the most by 12% and 7% month-on-month.
Over the past few months, India IT talent demand has been volatile across roles, cities, and industries. Talent demand is expected to continue to fluctuate as major Indian IT service providers lose contracts and enterprises explore more insourcing opportunities.
The demand for IT services in India jumped by 19% on a month-on-month basis after declining for two consecutive months. The year-on-year increase of 22% pointed to a significant uptick in hiring activities this month, rebounding from the slowness over the previous few months.
On a month-to-month basis, demand again surged in tier 2/3 cities compared to tier 1 cities. The increased reliance on tier 2/3 cities suggests a growing client preference for cost-effective IT service delivery locations.
Among tier 1 locations, Hyderabad and Kolkata bounced back the strongest with 36% and 35% growth in demand on a month-on-month basis. All locations in the three top tiers showed increased IT services demand – except for Pune, which dropped slightly.
Every major industry segment, except for banking, financial services, and insurance (BFSI), returned with increased demand. Service providers led the chart with a 22% increase in job demand compared to last month. However, BFSI declined 23% from the prior month.
The demand for IT services declined for two consecutive months after recording a 14-month high in June 2023. Demand fell by 16% month-on-month and 32% on a year-on-year basis. At a segment level, IT ADM and IT infrastructure declined from July.
This trend could be a result of a quick fix by employers to adjust for the hiring surge in the second quarter of 2023. If the pattern continues, employee attrition will rise. However, the demand will likely pick up in the next few months as the end of the year nears.
Tier 1 cities continue to experience a higher decline in demand than tier 2/3 cities on a month-on-month basis, indicating the preference by enterprises to leverage low-cost talent from tier 2/3 cities.
At a city level, Kolkata witnessed the sharpest decline in demand at 47% and had an all-time low in the last 20 months. Among leading tier 2/3 cities, Kochi and Thiruvananthapuram showed the least decline in month-on-month demand.
The surge in demand by industry sectors halted, with consumer packaged goods registering the greatest decline since July. Business and professional services also reversed the growth trend.
A slightly higher decline in month-on-month demand across service providers that has continued for several months now clearly indicates increased insourcing by enterprises.
While the month-on-month view showed a 9% drop in the IT services talent demand trend in India, demand grew 17% over the prior three months and by 32% year-on-year.
Tier 1 cities witnessed a relatively higher decline than tier 2/3 cities month-on-month, showcasing the increased leverage of tier 2/3 Indian cities. This trend is consistent across most tier 1 and tier 2/3 cities. Jaipur and Coimbatore are the only exceptions across tier 2/3 cities, showing 10% and 3% growth, respectively. Among tier 1 cities, Mumbai and Kolkata witnessed the highest decline, while Pune recorded the lowest decline of approximately 2%.
Service providers witnessed the highest decline of all industry verticals for IT services demand over the past year. Business and professional services and consumer packaged goods saw a slight uptick in demand.
The demand for IT services in India showed further recovery and grew by 15% compared to May 2023. For the first time in the last six months, demand also showed growth on a year-on-year basis (21% growth compared to June 2023). At a segment level, both IT ADM and IT infrastructure segments witnessed 14-month high demand levels in June 2023, with IT infra talent demand growing 40% on a year-on-year basis.
The growth trend, which started in May, is solidifying and was consistent across all cities, though the extent of recovery varied. Chennai saw a modest recovery, whereas Mumbai saw a significant spike in demand. We believe the demand surge in Mumbai may not be entirely due to net new demand but could be due to talent management/attrition challenges arising from the hybrid/in-office model and the need to back-fill resources.
The demand from service providers continues to grow, and we believe there is more focus on hiring laterals this year compared to the previous year, which saw a significant uptick in campus hiring. This increase could also be due to multiple large deals that are at play in the market and providers hiring in anticipation of winning large business in the medium term.
The demand for IT services in India showed a recovery in the month of May, growing by 34% compared to the previous month and staying flat compared to 2022. This spike compared to March and April could be attributed to buyers placing demand ahead of the summer in key onshore geographies, which tend to be slower from a business perspective. The increase in demand was consistent across both tier-1 and tier-2/3 cities; however, the recovery was much steeper for tier-1 cities (growing 14% YoY) compared to tier-2/3 cities (shrinking by 20% on a YoY basis). Among the tier-1 cities, all showed an uptick in demand; however, Pune set a demand record of a 17-month high. The service provider segment, while it showed recovery compared to the previous month, on a YoY basis, registered a 7% decline in demand. On similar lines, BFSI and technology & communications verticals continue to show a declining demand trend on a YoY basis.
The demand for IT services in India further shrunk by 17% in April, reaching a 16-month low, and declined by 29% on a year-on-year basis. The impact of the anticipated global economic slowdown is clearly visible in the latest demand trends.
The declining trend is consistent across both tier-1 and tier-2/3 cities. Among tier-1 cities, Chennai, followed by Delhi-NCR, witnessed the highest decline. Tier-2 cities saw an even higher decline on a year-on-year basis at 32%. At this point, the demand for IT services talent in India is almost 50% of the demand in January 2022. However, this trend needs to be observed over a slightly longer period. If this trend continues for a few more months, the already reduced attrition numbers are likely to come down further.
Being the first month of the new fiscal year for many leading India-heritage service providers, this indicates a not so good start to the year 2023-24, and declining talent demand is deeply correlated to reduced business growth.
After five consecutive months of demand growth/stability, the demand for IT services in India dropped significantly (21%) in March and by 36% on a year-on-year basis. The declining trend in March was consistent across all tier-1 cities, though Mumbai witnessed the lowest decline among all tier-1 cities.
The demand in tier-2/3 cities also reduced by 26% on a year-on-year basis. This overall declining trend is expected as Q1 2022 witnessed a significantly higher demand due to attrition and talent wars faced by the industry, and with the current economic environment, most companies are not in an expansion mode.
Stay tuned for regular monthly updates as we monitor the landscape of the India IT services industry demand market. We’ll continue to provide the latest insights and trends, so you stay well-informed on locations and workforce developments.
As customers’ needs evolve and businesses strive for greater efficiency, the importance of application transformation has substantially increased for enterprises. Enterprises are actively embracing transformation efforts to fully leverage emerging technologies and transition from outdated legacy systems. Amid ongoing macroeconomic uncertainty, European enterprises are prioritizing application transformation initiatives to unlock business value at every stage of their transformation. Furthermore, there is a persistent emphasis on sustainability, compliance, and regulatory adherence.
In response, service providers are enhancing their offerings through strategic partnerships with technology and platform providers and developing IPs to maximize RoI and gain enterprise confidence. Additionally, they are making substantial investments to expand their regional delivery centers in Europe to strengthen local service delivery and ensure better proximity to customers.

Contents:
In this report, we examine:
Scope:
The PEAK Matrix® provides an objective, data-driven assessment of service and technology providers based on their overall capability and market impact across different global services markets, classifying them into three categories: Leaders, Major Contenders, and Aspirants.

©2023 Everest Global, Inc. Privacy Notice Terms of Use Do Not Sell My Information
"*" indicates required fields