Is Managed Detection and Response (MDR) the Holy Grail for Cybersecurity Services?

With the meteoric rise in cyber attacks and cybersecurity talent shortage, Managed Detection and Response (MDR) can help enterprisesimprove incident detection, investigation, and response without more staffing. MDR provides a winning combination of technology, analytics, and human intelligence to improve cyber resiliency. Read on for recommendations for an effective cybersecurity approach. Contact us
for questions or to discuss this topic in more detail.
The cybersecurity outlook has shifted from business and IT-driven to the C-suite. Enterprise investments are now geared towards establishing cyber resiliency programs with holistic threat advisory, comprehensive monitoring, and faster response as the key building blocks.
Let’s take a look at the elements enterprises want in cybersecurity.
Strategic enterprise priorities for running an effective cybersecurity program

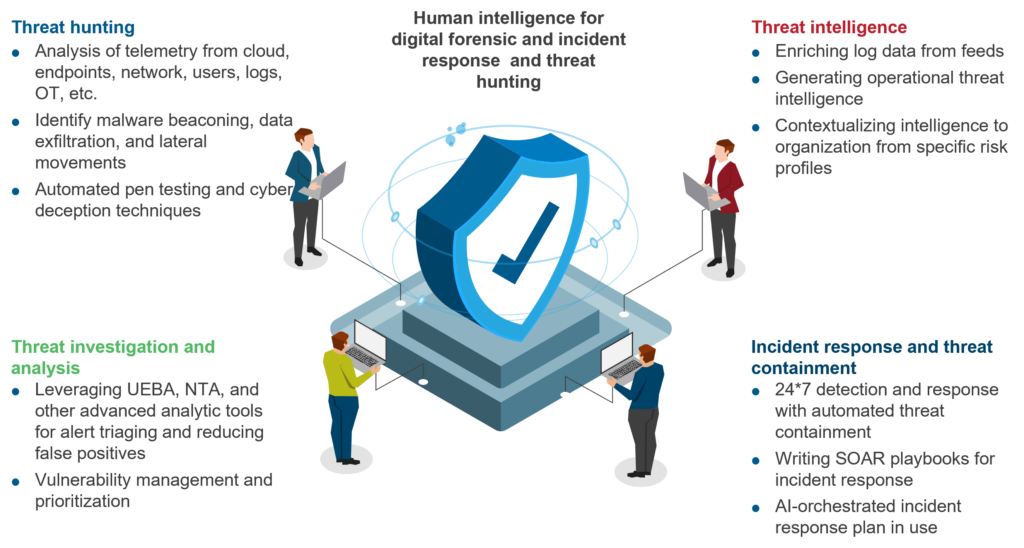
The MDR solution
With the right building blocks, MDR is becoming a near-term remedy for major enterprise cybersecurity challenges and helping companies meet their strategic priorities for effective cyber security programs.
Sophisticated threats are becoming difficult to detect because they can evade traditional controls and detection techniques. MDR aims to improve the struggling enterprise incident detection, investigation, and response capabilities.
MDR leverages next-generation technologies to hunt and respond better. Further, MDR brings the perfect amalgamation of technology, analytics, and human intelligence to bolster the enterprise cybersecurity position.
Types of managed detection and response providers
Our recent assessment of MDR services for leading technology enterprises analyzed the evolution of MDR technology vendors. We looked at their evolution from providing Endpoint Detection and Response (EDR) solutions to adding greater value through different services.
MDR service providers take different approaches to solutions and pricing services and can be classified in the following categories:
Type A vendors: They primarily position their EDR offerings as part of MDR services and typically provide an as-a-service model that includes the necessary software along with services
Type B vendors: These multi-threat vector-focused vendors cover not only endpoints but also include cloud-based workloads and networks in their solutions. They propose as-a-service and pure services models depending on the customer’s requirements and investment into detection and monitoring software in the current environment
Type C vendors: They are primarily managed security services providers delivering end-to-end security services along with MDR. In certain instances, they create bespoke offerings depending on customers’ requirements. They are typically vendor-agnostic and offer both as-a-service and a pure services model
Points to ponder before embracing MDR
Bringing together existing capabilities with an experienced provider is the key to jumpstarting the enterprise MDR journey.
Below are some recommendations to achieve success when implementing MDR services:
- Start small
- Add MDR capabilities to areas where your enterprise lacks capabilities or has an imminent need to scale existing capabilities
- Consider starting with incident response and threat remediation, given the lack of skilled resources and the required tools and technologies
- Integrate with existing technologies
- Undertake a comprehensive assessment to determine how the MDR provider’s threat containment and response approach can be best integrated with enterprise policies and business processes
- Integrate with existing security technologies quickly and based on standards (e.g., Application Programming Interface (API), protocols)
- Choose the right MDR stack and vendor
- Understand no single best MDR provider exists in the market. Select MDR providers that have experience in use cases relevant to the enterprise’s size, maturity, and industry vertical
- Choose a technology-agnostic vendor with a proprietary delivery platform with log and data management, analytics, orchestration, and incident response capabilities
Once enterprises have kickstarted their MDR journey, they often can choose to combine overall cybersecurity and MDR services under one portfolio. In a few instances, we have observed the supply side proposing the convergence of the Security Operation Center (SOC) into the MDR solution to help enterprises save costs. Enterprises should leverage MDR in a way that complements their existing operations to essentially fill the gaps in their threat management strategy.
Managed detection and response pricing
MDR pricing models and structures are still evolving. For example, Type A or Type C vendors usually prefer going with per unit-based pricing models where EDR and other software might or might not be included depending on requirements. Bespoke offerings can further modulate the price based on service inclusions and exclusions. Thus, different pricing metrics are offered, such as per asset, per user, etc., which slightly complicates matters and makes apples-to-apples comparisons difficult.
Additionally, we have observed that service providers may command premium prices because of the delivery location and type of value-adds included. For example, in the government sector, we have typically seen onshore delivery because of compliances, regulations, and discomfort with offshoring. At the same time, we have seen a few other cases where vendors leverage offshore locations for functions such as 24×7 monitoring to improve price positioning.
High-end threat hunting and cyber deception services are niche skills in the market. The current talent war creates a void in enterprise threat management strategy. Managed Detection and Response, with its suite of services, has the potential to emerge as a market winner.
Learn how to we can help you benchmark prices and contracts for a wide array of services, from contact center service IT to business processes. Our price benchmarking catalogs cover competitive market pricing for the most prominent locations across the globe.
To discuss Managed Detection and Response and cybersecurity, please reach out to [email protected], [email protected], and [email protected].