Blog
Now is the Time to Protect Operational Technology Systems from Cyber Risks

With growing digitalization and interconnected devices, Operational Technology systems that monitor and control industrial processes in critical infrastructure are increasingly vulnerable to cyber attacks. Learn about the OT security concerns enterprises face and key considerations for selecting an OT security provider in this blog.
Historically, IT and Operational Technology (OT) systems have been air-gapped, with little or no spending on Industrial Control Systems (ICS) security by enterprises. Further, most investments in industrial robots, SCADA, and PLC systems were made with a multi-decade horizon. This differs from IT investments, where the horizon is five years, and the technological refresh takes care of the security risk. Enterprises have been unwilling to touch OT systems because these big, monolithic systems ran well for many years, making security vulnerabilities and risks less of a priority to consider.
But OT systems – that power some of the nation’s most critical infrastructure – are at risk.
With the recent pandemic-driven digitization push and enterprises wanting to run resilient supply chains, these large monolithic untouched systems are now interconnected, making them highly prone to cyber attacks. These OT systems have also never been given basic security treatment of frequent patching, regular security updates, and periodic backups, which has further aggravated the issue.
Operational technology systems cyber attacks
Highly public cyber attacks on OT systems have raised awareness about the serious risks these security breaches can have on essential services, as seen in these industry-specific cases:
- Manufacturing – This segment had the second-highest ransomware-associated data extortion attacks in 2021. Traditionally, plant machinery and equipment have been designed for performance and not security. But stalled assembly lines or production units directly impact end buyers and can be disastrous for manufacturers
- Energy, utilities, and water – Threat actors have been targeting the most crucial elements in this critical infrastructure industry, mandating enhanced cybersecurity controls. Securing critical grid assets, substations, distribution pipelines, meters, etc., must be addressed
- Oil and gas – Digitizing operations for improved efficiency has increased the attack surface and has made this area more vulnerable to threats. During the Russia-Ukraine war, states were reportedly involved in sponsoring attacks, leading governments across the world to alter or create industry regulations and guidelines
Operational technology systems key challenges
The increasing connectivity of operational technology with external networks has further exacerbated the many OT security challenges enterprises face. Major OT security concerns include asset identification, misaligned IT and OT functions, OT threat and asset intelligence, patching legacy infrastructures, OT vulnerability management, and network segmentation.
Based on market conversations with more than 100 market participants, Everest Group identified and prioritized the following key enterprise challenges.
Technology vendor snapshot for OT security
 Source: Everest Group
Source: Everest Group
Specialist providers can help enterprises navigate security challenges related to OT and ICS. Enterprises should seek technology solutions that allow them to quickly identify vulnerabilities and prioritize actions to reduce and eliminate potential risks.
A provider of choice should offer a single platform for visibility and threat monitoring while ensuring seamless integration with existing enterprise technology investments. The below capabilities illustrate what enterprises should look for when selecting an OT security provider.
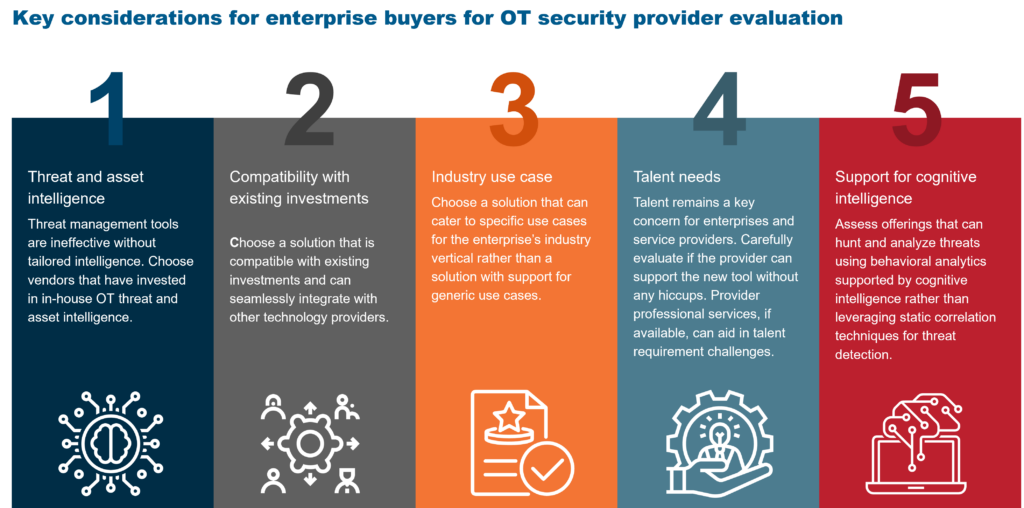
By investing in tools that can provide vital intelligence and partnering with providers that offer compatible, industry-specific solutions and a skilled talent pool, enterprises can begin to thwart the growing risks to OT systems – before it is too late.
To discuss Operational Technology Systems and OT security, please reach out to [email protected] and [email protected].
Explore the top five demand themes in technology services – data and AI, cloud, experience, platforms, and security – driving growth for IT service providers in 2023 in our upcoming webinar, IT Service Provider 2023 Forecast: The Top 5 Themes for Growth and Wallet Share.