Building a Resilient Supplier Cyber Risk Management Strategy

Sharing sensitive data with outsourcing providers in today’s interconnected digital world has increased organizations’ vulnerability to cyberattacks, making it more important than ever to have an effective supplier cyber risk management strategy. To protect against threats, read on to learn the best practices for supplier cyber risk management.
In today’s risky and interconnected environment, it has become essential for organizations to have a supplier cyber risk management strategy to identify, protect, detect, respond, and recover from supply chain cyberattacks.
The critical importance of relationships with outsourcing service providers has been amplified by the pandemic and recent geopolitical turmoil due to the Ukraine-Russia crisis. Outsourcing suppliers now play a vital role in running business operations, and these partnerships have grown more sophisticated.
With data sharing between the two parties increasing multifold, organizations have greater exposure to ransomware attacks, phishing, denial-of-service, and other cyberattacks.
Depending on the sensitivity of data shared with suppliers, the potential risk of data loss can impact an organization’s business operations – making it essential to develop a supply chain cyber risk management plan to protect from significant financial and operational impacts.
Not having a formal supplier cyber risk management strategy can cause compliance issues. With scrutiny on global supply chains intensifying, a lack of supplier insights can lead to government regulation violations, resulting in financial losses and tarnishing an organization’s brand.
As suppliers have access to sensitive and business-critical information, managing permissions and protecting data from unauthorized access, misuse, and data loss become crucial.
Further, many other risks exist from a supplier’s operational perspective, including issues related to geopolitics, bankruptcy, and macro risks. Organizations should have complete supply chain visibility to rapidly respond to susceptibilities and disruptions at the supplier’s end.
All of these factors can have a long-lasting impact on an organization’s image and reputation, potentially deteriorating customer loyalty and trust. Hence, having a resilient supplier cyber risk management strategy that includes visibility, transparency, clear communication, and collaboration has become non-negotiable for organizations.
The Everest Group risk management matrix
Let’s take a look at the different risk scenarios and their remedial measures below:
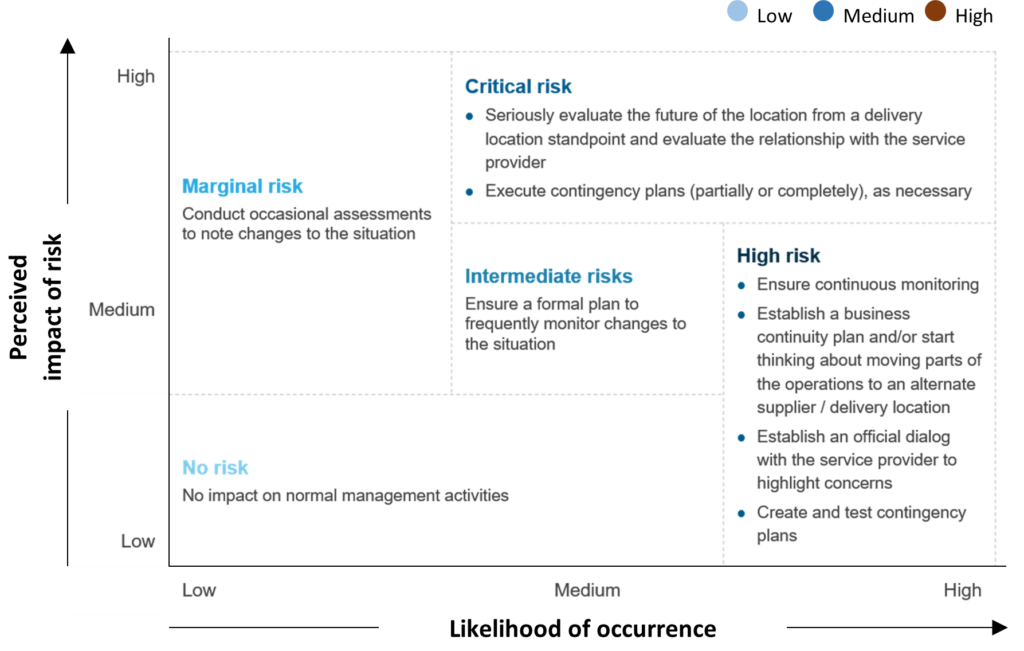
Exhibit 1: Everest Group Supplier Management Toolkit: Risk Management in Outsourcing
Best practices for developing a supplier cyber risk management strategy
Developing a Supply Chain Risk Management (SCRM) program is indispensable for organizations as they become increasingly vulnerable to supply chain attacks.
Currently, the risk management focus in outsourcing is limited to compliance requirements such as the Sarbanes-Oxley Act (SOX), Service Organization Control (SOC) certifications, industry-specific compliances such as Health Insurance Portability and Accountability Act (HIPAA) and Health Information Trust Alliance (HITRUST), and criminal background verifications.
Other vital factors such as geopolitical and offshoring risks have not yet become key executive priorities. Further, as more companies lean on service providers to drive digitalization and corresponding transformation in their outsourced processes, organizations rarely try to identify potential risks and establish associated mitigation/contingency plans.
Some industry best practices such as ISO/IEC 27036:2013 and the NIST Cybersecurity Framework have been updated to include information security for supplier relationships, highlighting the importance of SCRM in corporate security. In terms of cyber security, this involves:
- Defining cyber security requirements and measures that apply to suppliers based on their risk category
- Enforcing these requirements via formal agreements (e.g., contracts) to ensure suppliers enter a binding commitment
- Verifying and validating communication and access from and to suppliers
- Ensuring effective implementation of cyber security requirements
- Managing and supervising the above activities periodically
To optimally engage with and manage suppliers, the entire supplier life cycle should be organized into these three phases:
- Before and during the contracting phase – Screening suppliers before onboarding is essential for organizations to assess financial, operational, and reputational aspects. Procurement heads need to carry out background checks to ensure suppliers’ compliance status and performance viability. An exhaustive contract with legally binding responsibilities related to cyber security for both the organization and its suppliers should be created. This contract should define fundamental and high-level security requirements and privacy-based controls for supplier relationships at every point in the life cycle
- During the ongoing relationship – Once suppliers are onboarded, organizations must track all assets suppliers can gain entry to in a central repository. Customers should categorize suppliers into different risk classes based on how critical the information is to further define appropriate cybersecurity controls. These controls should be continuously evaluated to ensure adherence
- After the termination of the relationship – Offboarding a supplier requires disabling its logical and physical access, removing access to any data, and destructing it to ensure the supplier doesn’t hold any sensitive data. This phase also requires ensuring no severity incidents are pending and facilitating proper handoff between suppliers
Prevalence of risk management processes in the supplier life cycle
How common is it for organizations to have established risk management processes in each of the third-party life cycle steps? Our polling results show while most organizations have these safeguards in the first stage, fewer use them in later phases, as illustrated below:
Exhibit 2: Everest Group’s Webinar Quick Poll (Could Your Business Partners Be Offering More Risk than Support?)
The supply chain for almost any organizational procurement activity can be the target of cyberattacks, either by going after the supply chain or the supplier’s/organization’s systems, once they are integrated.
More complex and sophisticated attacks are often left undiagnosed or unreported, making them potentially more disastrous for enterprises. At different points in the supplier management life cycle, stakeholders across organizations will have the primary responsibility for establishing and maintaining effective supplier cyber security controls.
Vigorous governance is required to ensure relevant stakeholders are responsible at the right time to guarantee optimal and best efforts are made to combat any cyber threats. To complement this governance, a strong collaborative culture across different departments is needed to drive continuous improvement.
Learn how to create an effective program for your organization in our executive brief on Cybersecurity Risk Management in the Supplier Life Cycle, part of our supplier management toolkit.
Please reach out to [email protected] to gain further insights on supplier cyber risk management or Contact Us.
Discover even more about cybersecurity in our current environment in our webinar, Cybersecurity: What You Need to Know to Find the Right Partner and Price.