IT Talent
Post-quantum cryptography (PQC) has become essential for enterprises to protect against future quantum-enabled attacks and secure digital assets and sensitive data. Read on to discover providers’ crucial role in preparing enterprises for PQC. Reach out to explore this topic further.
As discussed in our previous blog, the emergence of quantum computing poses a significant threat to current public key cryptographic methods. When run on quantum computers – or more specifically, Cryptographically Relevant Quantum Computers (CRQCs) – some algorithms such as Shor’s can potentially break widely used methods like RSA, DSA, ECDSA, EdDSA, and DHKE, among others.
The advancement of quantum computers can seriously threaten data security and privacy for various enterprises, affecting fundamental principles such as confidentiality, integrity, and authentication. This makes it essential to reassess the security of these cryptographic methods.
The early and widespread use of quantum computers could wreak havoc, enabling new advanced cyberattacks that are impossible using classical computers. Post-quantum cryptography (PQC) is the solution to this problem. Let’s explore this further.
In the quantum computing era, PQC is vital in ensuring the long-term security of digital communication and data protection. PQC focuses on researching and adopting cryptographic algorithms that are ready for this era.
These algorithms are designed to be secure against both quantum and classical computers. Furthermore, they are expected to be deployable and integrable without significant modifications to current protocols and networks.
With extensive ongoing research in this field, researchers have proposed several mathematical schemes that meet the requirements for being potential candidates for quantum-safe cryptographic algorithms. These include lattice-based, multivariate polynomial, code-based, hash-based, and isogeny-based cryptography.
The U.S. Department of Commerce’s National Institute of Standards and Technology (NIST) launched a program in 2016 to create standardized quantum-safe cryptographic algorithms.
After a rigorous six-year evaluation involving global experts, it announced four finalists for quantum-safe cryptographic standards. The following algorithms selected by NIST address general encryption and digital signatures that are crucial for securing data exchanges and identity authentication:
| PQC algorithm | Cryptographic scheme | Purpose |
| CRYSTALS-Kyber | Lattice-based cryptography | Key encapsulation method (KEM) |
| CRYSTALS-Dilithium | Lattice-based cryptography | Digital signature |
| FALCON | Lattice-based cryptography | Small digital signature |
| SPHINCS+ | Hash-based cryptography | Digital signature |
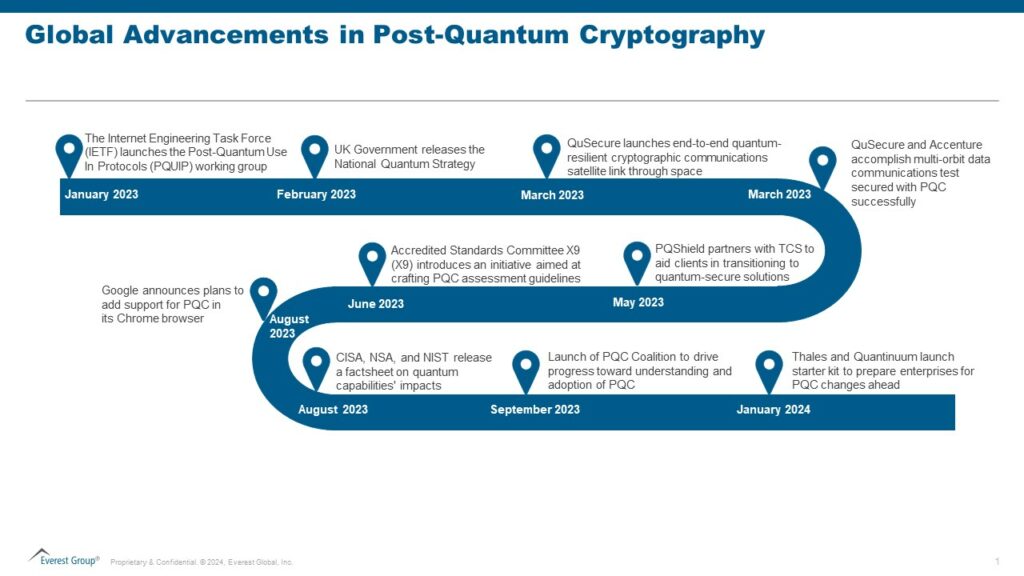
Several other developments related to PQC have occurred recently. The notable ones are highlighted below:
The complexity of cryptographic fields makes it difficult for enterprises to navigate data security. With numerous algorithms, protocols, and standards, enterprises often struggle to understand and implement robust cryptographic solutions.
Enterprises may encounter several common cryptographic pitfalls, including:
Enterprise considerations for embracing PQC
Considering the current challenges with cryptography, enterprises would face far more significant difficulties if they do not strategically plan for PQC. To prevent this, cybersecurity leaders globally must proactively prepare and initiate early plans to migrate to post-quantum cryptographic standards.
Taking a proactive stance is crucial since transitioning to new quantum-safe algorithms will be discontinuous, considering the inherent disparities in key size, error-handling properties, and other complexities.
Hence, enterprises should give themselves enough time to start small, experiment, learn from positive impacts and challenges, and explore ways to reduce technology transition costs.
Staying abreast of advancements in quantum computing and quantum-safe solutions is paramount. Enterprises must establish a comprehensive quantum readiness roadmap following these five steps:
Streamline the current cryptographic infrastructure: Enterprises can initiate modernization efforts by streamlining their current cryptographic infrastructure, including consolidating or replacing vendors to enable a managed migration process. The CFO should collaborate with other executives to prioritize PQC investments based on the risk appetite and strategic objectives and adopt a fully crypto-agile approach. Establishing a governance structure with clearly defined roles and responsibilities to adopt PQC effectively is also recommended.
There is an ongoing debate over some adversaries already gathering encrypted foreign communications, anticipating the future ability of quantum computers to decrypt such systems, and aiming to extract valuable secrets from the data collected. This threat, known as “harvest now, decrypt later,” highlights the urgency of making cryptographic changes rather than waiting.
As quantum computing advances, the demand for comprehensive quantum-resistant cryptographic solutions will only increase, favoring a ripe market for cybersecurity service providers to capitalize on.
PQC offers a significant opportunity for providers to position themselves as vital partners in ensuring the security and resilience of enterprises’ digital assets against the evolving quantum computing threats.
Leaders may need help understanding the advanced mathematical concepts and algorithms involved in PQC. The complexity of these cryptographic methods may need to be clarified for enterprises trying to grasp the intricacies of quantum-resistant solutions.
With all the latest discussions about quantum computers, service providers should take this time to develop a perspective on how PQC would impact enterprises from various industry verticals.
Providers should play an educational role, creating awareness about the risks posed by quantum computing and guiding enterprises on the importance of proactively transitioning to quantum-resistant solutions.
Service providers should develop strategies to hire, train, and upskill talent in PQC and quantum computing concepts. Additionally, they can invest in R&D initiatives to explore new approaches and solutions in the PQC field. By collaborating with relevant technology vendors, research institutions, and other organizations paving the way for PQC, service providers can foster innovation and help their clients stay at the forefront of technological advancements.
Cybersecurity service providers can offer specialized consultation and assessment services to help enterprises evaluate and inventory their current cryptographic infrastructure, prioritize components based on risk, identify vulnerabilities to quantum attacks, and recommend appropriate post-quantum cryptographic solutions.
Moreover, they can engage with enterprises on initial levels to develop comprehensive strategies for implementing and managing these solutions effectively, ensuring seamless integration with existing security frameworks and compatibility with legacy systems.
Service providers should prioritize PQC to address the threat quantum computing poses to traditional cryptographic systems. By embracing PQC, service providers can safeguard their clients’ data and infrastructure against potential quantum attacks.
Additionally, they can explore new use cases for PQC to unlock innovative solutions and stay ahead of the curve in the rapidly evolving quantum landscape. These new use cases may include:
PQC is no longer a theoretical concept but a reality. Multiple applications of PQC have emerged. In their latest release, OpenSSL has fully enabled PQC for digital signatures and fundamental establishment mechanisms. The Signal Protocol, an essential constituent of Signal, Google RCS, and WhatsApp messengers, has also announced support for the PQXDH protocol, becoming the first to introduce PQC for the initial key establishment. Apple has introduced a fresh encryption protocol named PQ3 for iMessage, offering advanced post-quantum security measures for instant messaging.
PQC is rapidly gaining traction for quantum-safe digital signatures, encryption, and fundamental exchange mechanisms. Its widespread adoption seems inevitable as the risks of quantum supremacy proliferate.
The standardized algorithms aren’t battle-tested yet, and exploitable weaknesses could be uncovered, leading to adjustments in their functioning or the development of entirely new algorithms.
We anticipate PQC becoming the cornerstone of cybersecurity strategies in the coming years. Moreover, the security standards are expected to recommend or mandate PQC.
PQC has become a crucial element of enterprise security, safeguarding against quantum-enabled attacks and ensuring the integrity and confidentiality of sensitive data.
Enterprises must start planning to migrate from a secure lock to an unbreakable vault: post-quantum cryptography! Service providers play a crucial role in guiding and supporting enterprises every step of the way.
To discuss post-quantum cryptography further, please contact Prabhjyot Kaur, Kumar Avijit, and Ronak Doshi.
Wealth Management Technology

Wealth Management
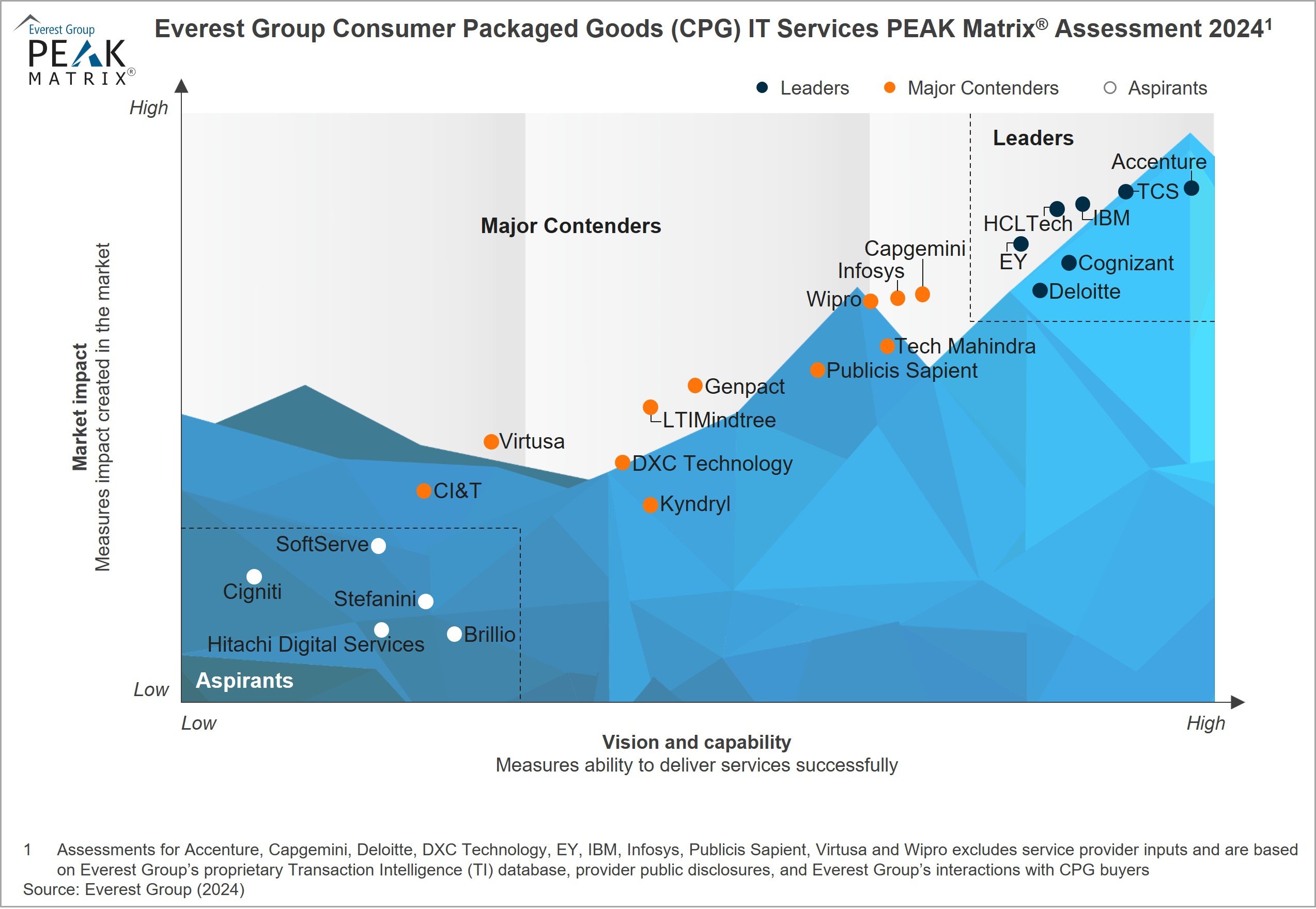
Despite economic uncertainties and margin pressures, Consumer Packaged Goods (CPG) enterprises are modernizing their IT systems across the entire value chain. These enterprises primarily focus on personalizing customer experience, streamlining supply chains, and emphasizing digital commerce using technologies such as AI/ML, cloud, IoT, and automation. Key priorities also involve fortifying data security, ensuring compliance, and automating manual processes to enhance overall efficiency. With widespread technology adoption, enterprises are increasingly leveraging digital strategies to enhance their competitive edge, increase operational efficiency, optimize processes, deliver personalized experiences to consumers, and drive growth.
Contents:
Scope
The PEAK Matrix® provides an objective, data-driven assessment of service and technology providers based on their overall capability and market impact across different global services markets, classifying them into three categories: Leaders, Major Contenders, and Aspirants.
Capital One’s planned US$35.3 billion acquisition of Discover Financial Services would combine two of the largest credit card companies, creating the most dominant US credit card firm. This deal holds the potential to significantly impact the banking and financial services (BFS) IT services market and providers. Read on to learn the looming risks and what to pay attention to.
Contact us to discuss the topic further.
Acquiring Discover would give Capital One access to a credit card network of more than 300 million cardholders. If the Capital One merger clears antitrust regulations, the combined entity would become the sixth-largest US bank by assets and a leading card issuer and network provider for the US payments market.
Let’s explore the following four implications of the Capital One merger on the BFS technology and IT services sectors.
Macroeconomic uncertainty and rising interest rates slowed financial services dealmaking in 2023. However, S&P predicts regional and community banks will be interested in mergers of equals this year. In these challenging times, banks want to understand the potential synergies of the merged entities clearly. They also require deeper due diligence than in the past, as exemplified by the failed merger of TD Bank Group and First Horizon.
Traditionally, acquisitions were an opportunity to enter new product lines and geographies, gain new capabilities, and achieve cost savings and operational efficiencies through technology modernization and streamlining processes and systems.
Recent banking sector acquisitions underscore a clear strategic focus on directing resources to targeted areas. Banks are divesting or seeking partners for non-core or insufficiently scaled units that lack a distinct competitive edge and demand substantial investment.
Our analysis indicates that merger and acquisition (M&A) activity among regional and community banks will increase, driven by the need to achieve greater scale. This strategic move is essential for these financial institutions to compete effectively with larger players, particularly as customer engagement transitions from physical to digital platforms.
By joining forces, these banks will be better positioned to develop new competencies in data management, AI/ML, open application programming interfaces (APIs), and advanced analytics, aligning with the growing digitalization of banking services. The merged entities will benefit from larger resource pools, facilitating improved alignment between skills and talent.
Discover and Capital One have traditionally relied heavily on outsourcing to two or three major service providers. In mergers, providers with significant contracts with both entities typically stand to lose revenue because spending by the merged entity will not be as large as it was under the separate relationships unless they gain wallet share from competitors.
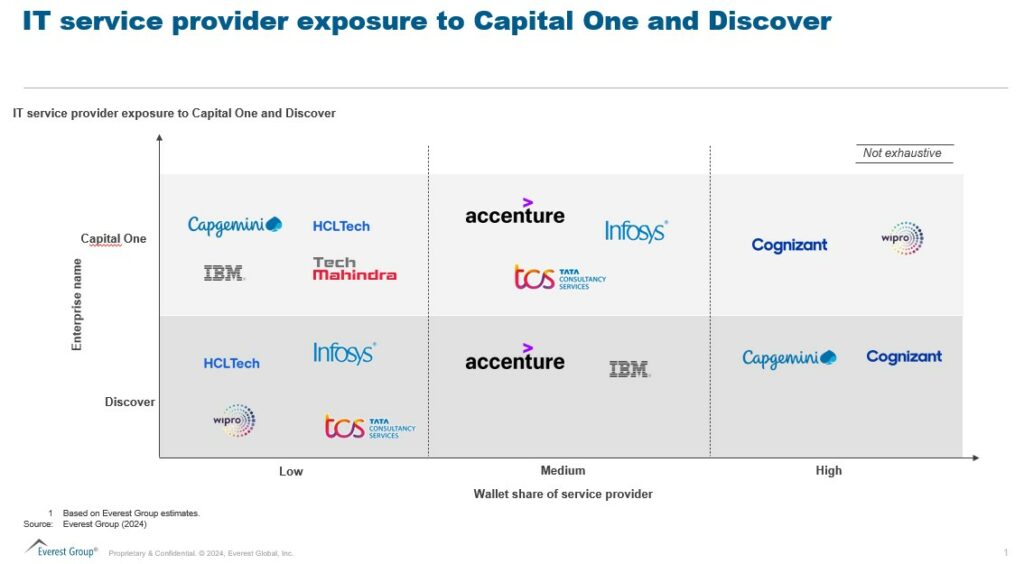
Suppliers that solely provide services to Discover are at risk of having their portfolio consolidated and moved to Capital One. However, providers who bring intellectual property or a niche capability may maintain the business through the consolidation.
Discussions about increased regulatory scrutiny are emerging, as even the regional banking market is at the cusp of such transactions. Moreover, this transaction can potentially increase competition for giants Mastercard and Visa.
M&As spur increased short-term spending on post-merger integration and consulting services. By rationalizing vendor portfolios and IT infrastructures, merged entities can substantially cut costs by eliminating redundant applications and platforms. BFS firms will need partners to devise modernization roadmaps to create long-term value.
Merged entities must swiftly adapt their operational models, delivery strategies, and sourcing decisions to excel in the evolving landscape. Investing in specific technologies and tools is essential to foster growth and ensure operational continuity. Emphasizing core operations becomes a prerequisite as firms assess the appropriate valuation before crafting their integration strategy.
The road ahead for the Capital One merger
Richard Fairbank, founder, chairman, and CEO of Capital One, has emphasized that the merger with Discover presents a unique opportunity to unite two highly successful companies with complementary strengths and franchises.
The Capital One merger aims to establish a payments network capable of rivaling the industry’s most extensive networks and companies. However, the potential impact of increased market concentration from this combination will face regulatory scrutiny.
Providers should closely monitor system integration opportunities, as Capital One plans to expand its 11-year technology transformation initiative to encompass all of Discover’s operations and network.
The new entity will invest in growth initiatives, including faster time-to-market, innovative products and experiences, and personalized real-time marketing efforts. Operationally, underwriting, efficiency, risk management, and compliance enhancements will drive data and technology investments.
We are closely watching the market and regulatory actions. To discuss the Capital One merger and its impact on the US banking landscape, reach out to Ronak Doshi, [email protected], Kriti Gupta, [email protected], or Pranati Dave, [email protected].
Join this webinar to hear our analysts discuss Global Services Lessons Learned in 2023 and Top Trends to Know for 2024.
View the event on LinkedIn, which was delivered live on Thursday, January 18, 2024.
The current scarcity of talent equipped with next-generation technology skills is leading enterprises to rely more on IT service providers for needed capabilities and creating a race for providers to attain top tech talent.
Watch this LinkedIn Live to learn the findings from our recent Talent Readiness for Next-generation IT Services PEAK Matrix® assessment, including insights into the technology talent market, key trends and emerging skills, and the current landscape.
The speakers also discuss IT service providers’ workforce management and development capabilities and talent portfolio rates, as well as provide best-in-class practices that leading IT service providers have adopted to build a sustainable pipeline of high-quality, multi-skilled talent.
What questions does the event answer for the participants?

Despite unfavorable macroeconomic conditions, retail enterprises are strategically investing in IT modernization initiatives throughout their value chains. These enterprises are focusing on enhancing customer experience through AI and data analytics, optimizing supply chains with technologies such as IoT and automation, and integrating e-commerce seamlessly.
Their priorities also include strengthening data security, ensuring compliance, and automating manual processes for improved efficiency. Retailers are investing in IT transformations to adapt to market trends, employ data-driven decision-making, and gain a competitive edge through innovation. Recognizing the necessity of agility in a dynamic market, they plan to utilize cutting-edge technology solutions and platforms to promptly respond to evolving consumer preferences and emerging trends.
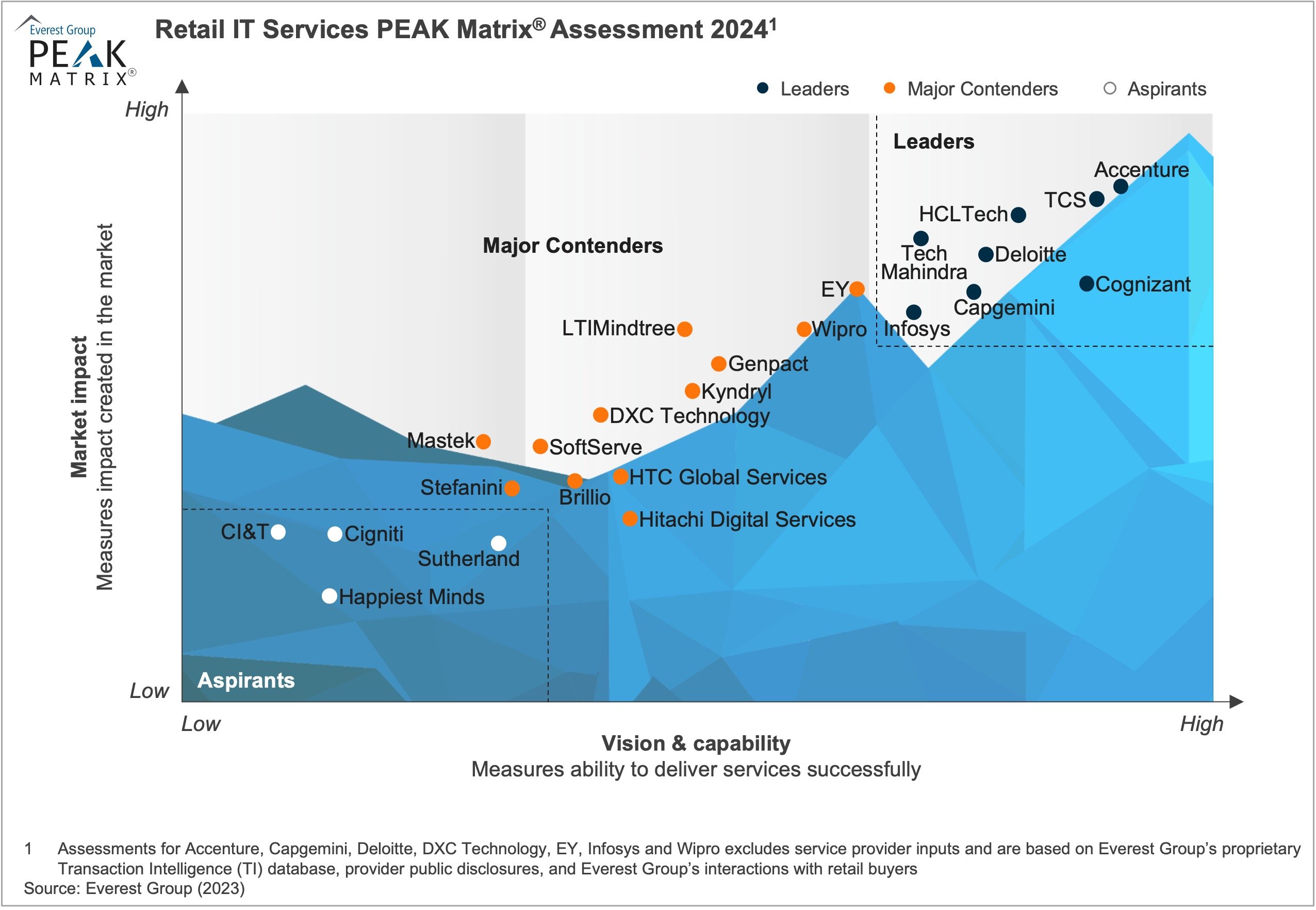
In this research, we present an assessment and detailed profiles of 24 service providers featured on the Retail IT Services PEAK Matrix®. Each provider profile provides a comprehensive picture of its service focus, key IP/solutions, domain investments, and case studies.
Contents:
Scope
The PEAK Matrix® provides an objective, data-driven assessment of service and technology providers based on their overall capability and market impact across different global services markets, classifying them into three categories: Leaders, Major Contenders, and Aspirants.

©2023 Everest Global, Inc. Privacy Notice Terms of Use Do Not Sell My Information
"*" indicates required fields